この大会は2018/4/6 5:00(JST)~2018/4/8 5:00(JST)に開催されました。
今回もチームで参戦。結果は1951点で780チーム中23位でした。
自分で解けた問題をWriteupとして書いておきます。
Welcome (Forensics 1)
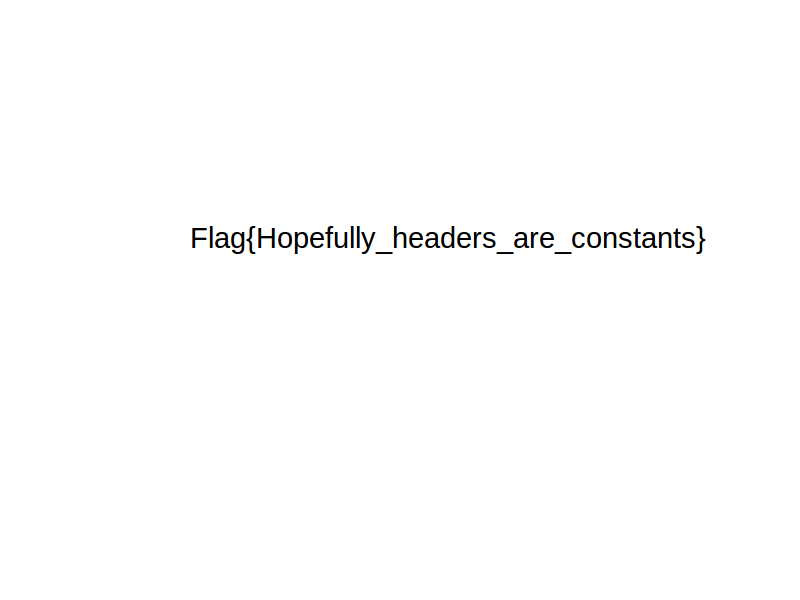
問題にフラグが書いてある。
sun{take_this_free_FLAG}
My Secret Stash (Forensics 100)
gitのファイル群が添付されている。
$ cd .git $ xxd -g 1 index 0000000: 44 49 52 43 00 00 00 02 00 00 00 01 5a ab 13 05 DIRC........Z... 0000010: 2f ad 33 86 5a ab 13 05 2f 55 fc 4e 01 00 00 04 /.3.Z.../U.N.... 0000020: 00 5d 74 3d 00 00 81 a4 00 00 01 f5 00 00 00 14 .]t=............ 0000030: 00 00 01 3c 9f ee ea b8 2f 7a fe 27 eb 0f 67 21 ...<..../z.'..g! 0000040: 2f 95 2d c8 6c 23 03 e9 00 07 73 65 63 72 65 74 /.-.l#....secret 0000050: 73 00 00 00 54 52 45 45 00 00 00 19 00 31 20 30 s...TREE.....1 0 0000060: 0a ce 69 c6 ab c7 c9 9b 63 50 5d f3 81 22 77 d6 ..i.....cP].."w. 0000070: 9b a4 67 4b 9d 8b 25 e0 4f a8 48 6f a2 6c c8 27 ..gK..%.O.Ho.l.' 0000080: 28 4e 8a 8f b8 2a 75 67 55 (N...*ugU $ python -c 'import zlib; print zlib.decompress(open("objects/9f/eeeab82f7afe27eb0f67212f952dc86c2303e9").read())' blob 316I'm so very sorry, you will not find my secrets in here. There was a time at which I wanted to share my secrets with someone, but that was long ago and I don't trust anyone anymore. I want to keep all of my secrets to myself for now on! Good luck trying to find them, there's nothing to find. hehehehehehehehe!!!!!! $ cat logs/refs/heads/master 0000000000000000000000000000000000000000 7e2927361b7e4101e07fc5a475bb244622a275e3 Carlos Staszeski <cstaszeski@gmail.com> 1521160193 -0400 commit (initial): vegan! 7e2927361b7e4101e07fc5a475bb244622a275e3 92fb7e7ebbc65d04ac311c3f1d4e496cd867e94d Carlos Staszeski <cstaszeski@gmail.com> 1521160586 -0400 commit: is 92fb7e7ebbc65d04ac311c3f1d4e496cd867e94d 3fe304a91a3049d9589e379b843f4dca9c47aafc Carlos Staszeski <cstaszeski@gmail.com> 1521160985 -0400 commit: Bobby $ python -c 'import zlib; print zlib.decompress(open("objects/7e/2927361b7e4101e07fc5a475bb244622a275e3").read())' commit 185tree 74967e81c7d6b83bb2647abc6890a3adfae0e96a author Carlos Staszeski <cstaszeski@gmail.com> 1521160193 -0400 committer Carlos Staszeski <cstaszeski@gmail.com> 1521160193 -0400 vegan! $ python -c 'import zlib; print zlib.decompress(open("objects/74/967e81c7d6b83bb2647abc6890a3adfae0e96a").read())' | xxd -g 1 0000000: 74 72 65 65 20 33 35 00 31 30 30 36 34 34 20 73 tree 35.100644 s 0000010: 65 63 72 65 74 73 00 8a de a5 38 cd 0f d8 27 09 ecrets....8...'. 0000020: 09 4b 9c 77 2d c3 a2 15 76 d4 d3 0a .K.w-...v... $ python -c 'import zlib; print zlib.decompress(open("objects/8a/dea538cd0fd82709094b9c772dc3a21576d4d3").read())' blob 225So, you've discovered how to travel back in time did you? Well that's not going to help you much here, you see, my stash is so well hidden you will never ever ever find it! hahahahahahahahhahahahahahahahahahahah!!!!!!!!!!!!! $ python -c 'import zlib; print zlib.decompress(open("objects/92/fb7e7ebbc65d04ac311c3f1d4e496cd867e94d").read())' commit 229tree ed91e6d10fdb88d4a9e2f4471e7b60170ba70a37 parent 7e2927361b7e4101e07fc5a475bb244622a275e3 author Carlos Staszeski <cstaszeski@gmail.com> 1521160586 -0400 committer Carlos Staszeski <cstaszeski@gmail.com> 1521160586 -0400 is $ python -c 'import zlib; print zlib.decompress(open("objects/ed/91e6d10fdb88d4a9e2f4471e7b60170ba70a37").read())' | xxd -g 1 0000000: 74 72 65 65 20 33 35 00 31 30 30 36 34 34 20 73 tree 35.100644 s 0000010: 65 63 72 65 74 73 00 94 7f 94 13 31 a9 eb 2d 90 ecrets.....1..-. 0000020: 87 05 45 34 89 cd 56 e0 61 7d a5 0a ..E4..V.a}.. $ python -c 'import zlib; print zlib.decompress(open("objects/94/7f941331a9eb2d908705453489cd56e0617da5").read())' blob 304I feel like we are becoming good friends you and I. Yes. I even considered letting you in on one of my secrets just now, but I didn't want to risk it falling into the wrong hands. So instead I stashed it away and destroyed it so that no one would ever be able to recover my secrets! muahahahahahah!!!!!! $ python -c 'import zlib; print zlib.decompress(open("objects/3f/e304a91a3049d9589e379b843f4dca9c47aafc").read())' commit 232tree ce69c6abc7c99b63505df3812277d69ba4674b9d parent 92fb7e7ebbc65d04ac311c3f1d4e496cd867e94d author Carlos Staszeski <cstaszeski@gmail.com> 1521160985 -0400 committer Carlos Staszeski <cstaszeski@gmail.com> 1521160985 -0400 Bobby $ python -c 'import zlib; print zlib.decompress(open("objects/ce/69c6abc7c99b63505df3812277d69ba4674b9d").read())' | xxd -g 1 0000000: 74 72 65 65 20 33 35 00 31 30 30 36 34 34 20 73 tree 35.100644 s 0000010: 65 63 72 65 74 73 00 9f ee ea b8 2f 7a fe 27 eb ecrets...../z.'. 0000020: 0f 67 21 2f 95 2d c8 6c 23 03 e9 0a .g!/.-.l#... $ python -c 'import zlib; print zlib.decompress(open("objects/9f/eeeab82f7afe27eb0f67212f952dc86c2303e9").read())' blob 316I'm so very sorry, you will not find my secrets in here. There was a time at which I wanted to share my secrets with someone, but that was long ago and I don't trust anyone anymore. I want to keep all of my secrets to myself for now on! Good luck trying to find them, there's nothing to find. hehehehehehehehe!!!!!!
フラグが見つからない。手あたり次第調べる。
$ python -c 'import zlib; print zlib.decompress(open("objects/7b/82ac03c49c0b55a4a8b8ffb3c04c5fe565fba6").read())' commit 258tree 74967e81c7d6b83bb2647abc6890a3adfae0e96a parent 7e2927361b7e4101e07fc5a475bb244622a275e3 author Carlos Staszeski <cstaszeski@gmail.com> 1521160299 -0400 committer Carlos Staszeski <cstaszeski@gmail.com> 1521160299 -0400 index on master: 7e29273 vegan! $ python -c 'import zlib; print zlib.decompress(open("objects/14/a5c7088e7638abb2232c8cac1c7dd4687819f0").read())' commit 304tree c9936edd0f107fc91fdaa876def0dc960b000760 parent 7e2927361b7e4101e07fc5a475bb244622a275e3 parent 7b82ac03c49c0b55a4a8b8ffb3c04c5fe565fba6 author Carlos Staszeski <cstaszeski@gmail.com> 1521160299 -0400 committer Carlos Staszeski <cstaszeski@gmail.com> 1521160299 -0400 WIP on master: 7e29273 vegan! $ python -c 'import zlib; print zlib.decompress(open("objects/c9/936edd0f107fc91fdaa876def0dc960b000760").read())' | xxd -g 1 0000000: 74 72 65 65 20 33 35 00 31 30 30 36 34 34 20 73 tree 35.100644 s 0000010: 65 63 72 65 74 73 00 bd 12 73 6e 7c 80 5c 83 49 ecrets...sn|.\.I 0000020: 4a 71 c3 66 a7 f8 85 0e e7 a3 79 0a Jq.f......y. $ python -c 'import zlib; print zlib.decompress(open("objects/bd/12736e7c805c83494a71c366a7f8850ee7a379").read())' blob 17sun{git_gud_k1d}
sun{git_gud_k1d}
Source Protection (RE 100)
https://sourceforge.net/projects/pyinstallerextractor/からPyInstaller Extractorをインストール、展開する。
>pyinstxtractor.py passwords.exe [*] Processing passwords.exe [*] Pyinstaller version: 2.1+ [*] Python version: 27 [*] Length of package: 3188825 bytes [*] Found 18 files in CArchive [*] Beginning extraction...please standby [+] Possible entry point: pyiboot01_bootstrap [+] Possible entry point: passwords [*] Found 194 files in PYZ archive [*] Successfully extracted pyinstaller archive: passwords.exe You can now use a python decompiler on the pyc files within the extracted directory
passwordsファイル内にフラグがあった。
sun{py1n574ll3r_15n7_50urc3_pr073c710n}
Visionary (Crypto 150)
スペースを除くprintableな文字をすべて使ったVigenere暗号。
chars = '!\"#$%&\'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqrstuvwxyz{|}~' with open('visionary/Cipher1.txt', 'r') as f: c1 = f.read().strip() with open('visionary/Decipher(Cipher1).txt', 'r') as f: p1 = f.read().strip() with open('visionary/cipherFlag.txt', 'r') as f: encFlag = f.read().strip() key = '' for i in range(len(encFlag)): index = chars.index(c1[i]) - chars.index(p1[i]) if index < 0: index += len(chars) key += chars[index] print key flag = '' for i in range(len(encFlag)): index = chars.index(encFlag[i]) - chars.index(key[i]) if index < 0: index += len(chars) flag += chars[index] print flag
sun{Why_would_Any0n3_use_A_T@bl3_tH@t_LaRg3}
Missing Bytes (Scripting 200)
再帰を使いながら、ディレクトリのサイズが配下のサイズの合計と一致しない場合にsendコマンドでディレクトリ名を指定する。
コードは以下の通り。20ラウンド正解すると、フラグが表示される。
import socket import re def recvuntil(s, tail): data = '' while True: if tail in data: return data data += s.recv(1) def check_dir(name, size): # 0: ok # 1: ng # 2: finish cmd = 'cd ' + name #print cmd s.sendall(cmd + '\n') data = recvuntil(s, '$ ') #print data cmd = 'ls' #print cmd s.sendall(cmd + '\n') data = recvuntil(s, '$ ') #print data rows = data.split('\r\n') num = get_entries_num(rows[0]) sum_size = 0 for i in range(num): name2, fd, size2 = get_row_info(rows[i+1]) sum_size += size2 if fd == 'DIR': res = check_dir(name2, size2) if res == 1: s.sendall('send ' + name2 + '\n') data = recvuntil(s, '\n') data += recvuntil(s, ' ') if 'Hooray!' in data: data += recvuntil(s, '\n') data += recvuntil(s, '\n') print data return 2 else: data += recvuntil(s, '$ ') #print data elif res == 2: return 2 cmd = 'cd ..' #print cmd s.sendall(cmd + '\n') data = s.recv(256) #print data if size == sum_size: return 0 else: return 1 def get_entries_num(row): m = re.search('\((.+) entries\)', row) num = int(m.group(1)) return num def get_row_info(row): name = row[:7].strip() fd = row[8:12].strip() size = int(row[13:]) return name, fd, size s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect(('chal1.sunshinectf.org', 30001)) data = recvuntil(s, '\n') print data print 'start' s.sendall('start\n') for i in range(20): print '**************************' print '******** Round %02d ********' % (i+1) print '**************************' data = recvuntil(s, '$ ') print data cmd = 'ls' print cmd s.sendall(cmd + '\n') data = recvuntil(s, '$ ') print data rows = data.split('\r\n') num = get_entries_num(rows[0]) for j in range(num): name, fd, size = get_row_info(rows[j+1]) if fd == 'DIR': print name res = check_dir(name, size) if res == 1: s.sendall('send ' + name + '\n') data = recvuntil(s, '\n') data += recvuntil(s, ' ') if 'Hooray!' in data: data += recvuntil(s, '\n') data += recvuntil(s, '\n') #print data break else: data += recvuntil(s, '$ ') #print data elif res == 2: break
sun{a11_ur_byt3s_4re_b3long_t0_m3}