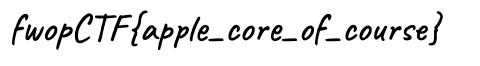この大会は2021/10/23 9:00(JST)~2021/11/1 0:00(JST)に開催されました。
今回もチームで参戦!といっても実質1人チームでした。
結果は29900点の満点で386チーム中4位でした。
自分で解けた問題をWriteupとして書いておきます。
Warm Up -- Let's Start! (General 100)
問題にフラグが書いてあった。
fwopCTF{this_is_the_flag}
Base2 (General 100)
2進数にする問題。
>>> bin(0xe8)[2:]
'11101000'
11101000
Base64 Abridged (General 100)
base64エンコードする問題。
$ echo -n "I love CTF" | base64
SSBsb3ZlIENURg==
SSBsb3ZlIENURg==
Touch the base (General 100)
base64デコードする問題。
$ echo ZndvcENURntiYXNlNjRfaXNfZXZlcnl3aGVyZX0= | base64 -d
fwopCTF{base64_is_everywhere}
fwopCTF{base64_is_everywhere}
Hex the way in (General 100)
ASCIIコードの16進数表記をデコードする問題。
>>> s = '66 77 6f 70 43 54 46 7b 62 61 63 6b 5f 66 72 6f 6d 5f 68 65 78 7d'
>>> s.replace(' ', '').decode('hex')
'fwopCTF{back_from_hex}'
fwopCTF{back_from_hex}
Zeros and Ones (General 100)
2進数をASCIIコードとしてデコードする。
enc = '01100110 01110111 01101111 01110000 01000011 01010100 01000110 01111011 01100011 01101111 01101101 01110000 01101100 01101001 01100011 01100001 01110100 01100101 01100100 01111101'
enc = enc.split(' ')
flag = ''
for c in enc:
flag += chr(int(c, 2))
print flag
fwopCTF{complicated}
Assembly Warm Up (General 100)
symbolic machine code と呼ばれる言語を答える問題。
Assembly
Jon Us in Discord (General 100)
Discordに入り、#generalチャネルのトピックを見ると、フラグが書いてあった。
fwopCTF{fweefwop_ctf_go_go_go}
Name this language(0) (General 150)
以下のプログラム言語を答える問題。
#include <stdio.h>
int main() {
printf("Hello, World!");
return 0;
}
C
Name this language (1) (General 150)
以下のプログラム言語を答える問題。
fn main() {
println!("Hello World!");
}
rust
Name this language (2) (General 150)
以下のプログラム言語を答える問題。
package main
import "fmt"
func main() {
fmt.Println("hello world")
}
go
Name this language (3) (General 150)
以下のプログラム言語を答える問題。
PROGRAM Triangle
IMPLICIT NONE
REAL :: a, b, c, Area
PRINT *, 'Welcome, please enter the&
&lengths of the 3 sides.'
READ *, a, b, c
PRINT *, 'Triangle''s area: ', Area(a,b,c)
END PROGRAM Triangle
FUNCTION Area(x,y,z)
IMPLICIT NONE
REAL :: Area
REAL, INTENT( IN ) :: x, y, z
REAL :: theta, height
theta = ACOS((x**2+y**2-z**2)/(2.0*x*y))
height = x*SIN(theta); Area = 0.5*y*height
END FUNCTION Area
Fortran
Name this language (4) (General 150)
以下のプログラム言語を答える問題。
IDENTIFICATION DIVISION.
PROGRAM-ID. FweefwopProgram.
PROCEDURE DIVISION.
DisplayPrompt.
DISPLAY "Fweefwop Wins!".
STOP RUN.
COBOL
Name this language (5) (General 150)
以下のプログラム言語を答える問題。
(defun fibonacci(n)
(cond
((eq n 1) 0)
((eq n 2) 1)
((+ (fibonacci (- n 1)) (fibonacci (- n 2))))))))
lisp
Name this language (6) (General 100)
以下のプログラム言語を答える問題。
LET N=10
20 FOR I=1 TO N
30 PRINT "FweeFwop is FweeFwoping"
40 NEXT I
BASIC
Name this language (7) (General 150)
以下のプログラム言語を答える問題。
size([],0).
size([H|T],N) :- size(T,N1), N is N1+1.
Prolog
Name this language (8) (General 150)
以下のプログラム言語を答える問題。
let sv (h:t) = p : sv (filter (\x -> x `mod` h /= 0) t) in sv [2..]
Haskell
What's that thing? (0) (General 150)
人間が読めるプログラムを実行可能なマシンコードに変換するのは何かという問題。
compiler
What's that thing? (1) (General 150)
プロセスの一種で、長い間とどまる傾向があり、通常自分では消えない。またsshでドアをノックすると、ドアに応答するということがあるようなものは何かという問題。
daemon
What's that thing? (2) (General 150)
ルーターはレイヤー3で機能し、IPアドレスを処理するが、レイヤー2で動作し、Macアドレスを処理するものは何かという問題。
Switch
What is that thing? (3) (General 150)
無効にすると、pingは機能しないものをフルネーム(4ワード)で答える問題。
Internet Control Message Protocol
Assembly: MOV and ADD (General 150)
mov eax, 0x0902F
add eax, 0x00138
上記のコード実行後、EAXの値を10進数で答える問題。
>>> 0x0902F + 0x00138
37223
37223
MOV again (General 150)
mov eax, 0x1111
mov ebx, 0x2222
mov eax, ebx
上記のコード実行後、EBXの値を10進数で答える問題。
>>> 0x2222
8738
8738
Shift (General 150)
mov eax, 0x123
shr eax, 4
shl eax, 8
上記のコード実行後、EBXの値を16進数(0x????)で答える問題。
>>> eax = 0x123
>>> eax >>= 4
>>> eax <<= 8
>>> hex(eax)
'0x1200'
0x1200
Assembly: Reset a register (General 150)
??? rax, rax
レジスタraxをリセット(値を0に設定)することができる演算子を答える問題。
xor
Assembly: Stack (1) (General 150)
mov eax, 0x123
mov ebx, 0x321
push eax
add eax, 0x111
mov ebx, eax
pop ebx
上記のコード実行後、EBXの値を16進数(0x????)で答える問題。
最終的にpushしたeaxの値をpopしている。
0x123
Assembly: Stack (2) (General 150)
mov eax, 0x123
mov ebx, 0x321
push eax
push ebx
pop eax
pop ebx
上記のコード実行後、EBXの値を16進数(0x????)で答える問題。
eaxとebxに格納した値が入れ替わっている。
0x123
XOR warm up (General 200)
すべての文字を\x01とXORする。
enc = 'gvnqBUGzyns^stmdr|'
flag = ''
for c in enc:
flag += chr(ord(c) ^ 1)
print flag
fwopCTF{xor_rules}
Modular (0) (General 200)
そのまま計算するだけ。
>>> 3 * 6 % 7
4
4
Modular (1) (General 200)
inverseを使って剰余環上の割り算をする。
from Crypto.Util.number import *
ans = 46 * inverse(11, 59) % 59
print ans
3
Modular (2) (General 200)
modulusの数値が小さいので、ブルートフォースする。
p = 607
for x in range(p):
if pow(x, 2, p) == 2:
print x
break
194
Modular Math (3) (General 150)
ブルートフォースで求める。
for p in range(1, 7001):
if pow(5, p, 7001) == 1:
print p
break
3500
Modular Math (4) (General 400)
m = 31,
e = 2813771283
n = 384302
とする。
pow(m, pow(m, e)) % n
= pow(m, pow(m, e, phi), n)
n = 384302 = 2 * 17 * 89 * 127
phi = 1 * 16 * 88 * 126
以上のことから計算する。
m = 31
e = 2813771283
n = 384302
phi = 1 * 16 * 88 * 126
ans = pow(m, pow(m, e, phi), n)
print ans
278505
NASM (1) (General 250)
asmファイルが添付されている。
$ nasm -f elf64 hello.asm -o hello.o
$ ld -m elf_x86_64 hello.o -o hello
$ ./hello
fwopCTF{i_have_done_this_ex}
fwopCTF{i_have_done_this_ex}
NASM (2) (General 200)
NASM (1)の問題のasmファイルを1文字修正して、"fwopCTF{i_have_done_this_exercise}"と出力されるようにするには、何に修正するかを答える問題。
以下の部分の0x13がdbから切り出すサイズ。
:
mov rax, 1 ; system call for write
mov rdi, 1 ; file handle 1 is stdout
mov rsi, message ; address of string to output
mov rdx, 0x13 ; number of bytes
syscall ; invoke operating system to do the write
:
message: db "i_have_done_this_exercise_i_swear_but_who_knows" 0x13を0x19にすればよい。
9
Go through some gates (General 300)
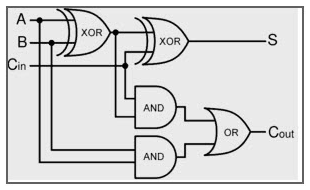
A, B, Cが1の場合、Sの値は何になるかを答える問題。
左上のXORで0、次のXORで1になり、Sは1になる。
1
Assembly: Jump (General 400)
asmファイルが添付されているが、バグがある。asmファイルの以下の箇所を修正してコンパイルする。
■_startの識別が一致させる。
1行目
global start
↓
global _start
■出力バイト数を13にする
33行目
mov edx, 0x0? ; number of bytes
↓
mov edx, 0x0d ; number of bytes$ nasm -f elf64 jump.asm -o jump.o
$ ld -m elf_x86_64 jump.o -o jump
$ ./jump
fwopCTF{fwop}
fwopCTF{fwop}
$ strings garden.jpg | grep fwop
Here is a flag "fwopCTF{Beneath_the_surface}".
fwopCTF{Beneath_the_surface}
Just inflate me (Forensics 100)
$ gzip -dc flag.txt.gz
fwopCTF{ok_you_found_me}
fwopCTF{ok_you_found_me}
The Meta Joke (Forensics 100)
$ exiftool MyCoolCard.jpg | grep fwop
Image Description : fwopCTF{metadata_is_funky}
fwopCTF{metadata_is_funky}
Not Viewable (Forensics 100)
$ file fflag.txt
fflag.txt: PNG image data, 405 x 38, 8-bit/color RGBA, non-interlaced
$ mv fflag.txt flag.png
pngとして画像を開く。

fwopCTF{actually_an_image}
Reading between the Eyes (Forensics 150)
$ zsteg Husky.png
b1,r,lsb,xy .. text: "7U>c[rvyzrfM\""
b1,rgb,lsb,xy .. text: "fwopCTF{r34d1ng_b37w33n_7h3_by73s}/"
b1,abgr,msb,xy .. text: "[U[wwyUU"
b3,b,lsb,xy .. text: "?rc%Gw'["
b3,rgb,lsb,xy .. file: PGP\011Secret Key -
b3,rgba,lsb,xy .. file: PGP\011Secret Key -
b4,r,lsb,xy .. text: "wxfveD#0"
b4,g,lsb,xy .. text: "TETETffx"
b4,b,lsb,xy .. text: "fwvB34\"TC "
b4,rgba,lsb,xy .. text: "O`/`/q_`O`O_?N/N"
fwopCTF{r34d1ng_b37w33n_7h3_by73s}
Not the same (Forensics 150)
2つのテキストファイルが与えられている。似て非なるものなので、差分をとる。
$ diff t1.txt t2.txt
122c122
< f
---
> .
583c583
< w
---
> .
651c651
< o
---
> .
2192c2192
< p
---
> .
2559c2559
< C
---
> .
2758c2758
< T
---
> .
2768c2768
< F
---
> .
2898c2898
< {
---
> .
3650c3650
< r
---
> .
3703c3703
< 3
---
> .
3891c3891
< s
---
> .
4089c4089
< p
---
> .
4297c4297
< 3
---
> .
4304c4304
< c
---
> .
4341c4341
< t
---
> .
4599c4599
< _
---
> .
5314c5314
< t
---
> .
7154c7154
< h
---
> .
8006c8006
< 3
---
> .
8048c8048
< _
---
> .
8110c8110
< d
---
> .
8390c8390
< 1
---
> .
8398c8398
< f
---
> .
8499c8499
< f
---
> .
9002c9002
< }
---
> .
fwopCTF{r3sp3ct_th3_d1ff}
Sharper Image (Forensics 150)
base64のデータが添付されているが、jpgのものと推測できる。このデータをデコードしてみる。
with open('bb.txt', 'r') as f:
data = f.read()
with open('flag.jpg', 'wb') as f:
f.write(data.decode('base64'))
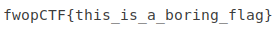
デコードした画像を見てみると、フラグが書いてあった。
fwopCTF{this_is_a_boring_flag}
What's inside of this apple? (Forensics 200)
Stegsolveで開き、[Analyse]-[Data Extract]でRGBのLSBを抽出すると、別のPNGが抽出できる。
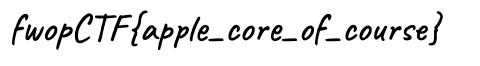
この画像にフラグが書いてあった。
fwopCTF{apple_core_of_course}
Follow the Shiba (Forensics 200)
$ zsteg shiba_with_message.png
b1,rgb,lsb,xy .. text: "No flag here, but you can check out https://imgur.com/gallery/jCJcbzZ "
b2,r,msb,xy .. text: "WUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUU"
b2,g,msb,xy .. text: ["U" repeated 209 times]
b2,b,lsb,xy .. text: "ADPUPQ@QP"
b2,abgr,msb,xy .. text: "[{s[SSsSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSS"
b4,r,msb,xy .. text: ["w" repeated 165 times]
b4,g,lsb,xy .. text: "wgvfvgvfvwffvwffggfgvwvfwwvvfgffwgfgwgvgwwfgvwvfwgvvvgfwgwvfwwvvvgvgwwvgvwffwgvwwwvgvvfgvgfwfgffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff"
b4,g,msb,xy .. text: ["f" repeated 162 times]
b4,b,lsb,xy .. text: "EDTDUDEEUDETUEUEUDEDUEDDTDUETDUEUDEETDEETDEUUEDDTEEDTETTUDUUUDUETDUEUDDUUDETUDEDTDUTDDUETEUTTDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDD"
b4,b,msb,xy .. text: "**\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\"\""
https://imgur.com/gallery/jCJcbzZにアクセスし、画像をダウンロードする。この画像に対してzstegで確認してみる。
$ zsteg undefined\ -\ Imgur.png
b1,rgb,lsb,xy .. text: "here is the flag fwopCTF{steg_is_fun}"
b2,r,msb,xy .. text: "]UUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUU"
b2,g,msb,xy .. text: ["U" repeated 231 times]
b2,b,msb,xy .. text: "}_UUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUU"
b2,rgb,msb,xy .. text: ["U" repeated 182 times]
b2,bgr,msb,xy .. text: ["U" repeated 182 times]
b2,abgr,msb,xy .. text: "wWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWW"
b3,bgr,msb,xy .. file: MPEG ADTS, layer I, v2, 96 kbps, Monaural
b3,abgr,msb,xy .. file: MPEG ADTS, layer I, v2, 112 kbps, Monaural
b4,r,msb,xy .. text: ["w" repeated 207 times]
b4,g,msb,xy .. file: MPEG ADTS, layer I, v2, 112 kbps, Monaural
b4,b,msb,xy .. text: ["w" repeated 207 times]
b4,rgb,msb,xy .. text: ["w" repeated 108 times]
b4,bgr,msb,xy .. text: ["w" repeated 108 times]
fwopCTF{steg_is_fun}
Pranked (Forensics 200)
リダイレクトされるが、linkを「リンクのアドレスをコピー」すると、元々のURLがわかる。
https://tinyurl.com/easilypranked
fwopCTF{easilypranked}
What is in this Cookie? (Forensics 200)
$ zsteg download_3.png
b1,r,lsb,xy .. text: "?{w((((((((7U="
b1,g,lsb,xy .. text: ["A" repeated 8 times]
b1,b,lsb,xy .. text: "\n\n\n\n\n\n\n\n_"
b1,b,msb,xy .. text: "APPPPPPPP"
b1,rgb,lsb,xy .. text: "Where is the flag? It must be here somewhere.\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\nFwopCTF{ThisIsSoMuchFun}"
b1,rgb,msb,xy .. text: "tPPPPPPPPPPPPPPPPPPPPPPPPb"
b2,b,msb,xy .. text: "W!UwUsUwUw"
b2,bgr,msb,xy .. text: "V75uQVWwuuA"
b2,abgr,msb,xy .. text: ["S" repeated 8 times]
b3,rgba,lsb,xy .. text: "?7sw3q?3s?"
b4,r,msb,xy .. text: "UUUU3UUU"
b4,g,msb,xy .. text: "wwwwwww7sww"
b4,b,msb,xy .. text: ["w" repeated 9 times]
b4,rgb,msb,xy .. text: "gy^gu^ouVo}1"
b4,bgr,msb,xy .. text: "viW~e_~e_vm7q"
FwopCTF{ThisIsSoMuchFun}
Bitcoin Laundering (0) (Forensics 200)
jsonデータが添付されている。このデータからトランザクション数を答える。
"}," を"},\n"に置換すると、20000行のデータになった。
20000
Bitcoin Laundering (1) (Forensics 400)
アドレス16ftSEQ4ctQFDtVZiUBusQUjRrGhM3JYweが受け取ったBitcoinの総量を答える問題。
jsonデータとして読み込み、'dest_addr'が'16ftSEQ4ctQFDtVZiUBusQUjRrGhM3JYwe'で、'cryptocurrency'が'Bitcoin'になっている'quantity'の合計を計算する。
import json
with open('transactions.json') as f:
dic = json.load(f)
sum = 0
for d in dic:
if d['dest_addr'] == '16ftSEQ4ctQFDtVZiUBusQUjRrGhM3JYwe' \
and d['cryptocurrency'] == 'Bitcoin':
sum += d['quantity']
print(sum)
63382.93
Apples & Oranges (Forensics 250)
$ steghide extract -sf Apple.jpg -p oranges
wrote extracted data to "secret.txt".
$ cat secret.txt
fwopctf{which_is_your_favorite}
fwopctf{which_is_your_favorite}
Wood Door (Forensics 250)
Stegsolveで開き、Blue plane 2を見ると、フラグが現れた。

fwopCTF{hiding_in_bit_plane}
Noise (Forensics 250)
Sonic Visualiserで開き、スペクトログラムを見る。

FWOPY
Corrupted_File (Forensics 300)
pngヘッダが壊れているので、修正する。
89 24 00 32 -> 89 50 4e 47
ihdrの長さが間違っているので、修正する。
00 00 00 12 -> 00 00 00 0d
すると、修正した画像にフラグが書いてあった。

fwopCTF{c0rrupted}
Smashed (Forensics 300)
たくさんデータがあるが、データの2個目をインデックスとすると、同じインデックスに対応する文字はすべて同じなので、インデックスの順に文字を並べる。
with open('smashed.txt', 'r') as f:
data = eval(f.read().rstrip())
m = [''] * 256
for d in data:
m[d[1]] = d[0]
msg = ''.join(m)
print msg
実行結果は以下の通り。
The Fweefwop CyberSecurity Team is honored to have you participate our first CTF.
We sincerely hope you had fun and learned something useful. Oh! the flag is
fwopCTF{kirby_is_the_best_in_super_smash_bros_change_my_mind}
fwopCTF{kirby_is_the_best_in_super_smash_bros_change_my_mind}
Kevin zzZZ (Forensics 400)
$ binwalk kevin_zzZZ.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
2227057 0x21FB71 PNG image, 1147 x 1147, 8-bit/color RGB, non-interlaced
2227116 0x21FBAC Zlib compressed data, default compression
2308197 0x233865 JPEG image data, JFIF standard 1.01
$ foremost kevin_zzZZ.jpg
Processing: kevin_zzZZ.jpg
|*|

pngが抽出でき、その画像にはQRコードが書いてある。読み取ると、フラグが現れた。
fwopCTF{rick_fan_are_you_not?}
$ ssh level0@linux.fweefwop.club
The authenticity of host 'linux.fweefwop.club (34.127.83.18)' can't be established.
ECDSA key fingerprint is SHA256:sm7uInZJMRlNFh5KAi4EP4tNjToVnp4HfK2+Qt4LHRM.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added 'linux.fweefwop.club,34.127.83.18' (ECDSA) to the list of known hosts.
level0@linux.fweefwop.club's password:
Linux fweefwoplinux 4.19.0-17-cloud-amd64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Oct 23 13:01:37 2021 from 34.127.83.18
level0@fweefwoplinux:~$ ls -la
total 28
dr-x------ 3 level0 level0 4096 Oct 18 01:31 .
drwxr-xr-x 15 root root 4096 Oct 18 00:12 ..
-r-------- 1 level0 level0 5 Oct 18 01:26 .bash_history
-r--r--r-- 1 level0 level0 220 Apr 18 2019 .bash_logout
-r--r--r-- 1 level0 level0 3526 Apr 18 2019 .bashrc
dr-x--x--x 3 level0 level0 4096 Oct 18 01:25 .gnupg
-r-xr-xr-x 1 level0 level0 807 Apr 18 2019 .profile
-r--r--r-- 1 root root 0 Oct 18 01:29 fwopCTF{level_1_u3xe4}
-rw-r--r-- 1 root root 0 Oct 18 01:31 xx
fwopCTF{level_1_u3xe4}
$ ssh level1@linux.fweefwop.club
level1@linux.fweefwop.club's password:
Linux fweefwoplinux 4.19.0-17-cloud-amd64 #1 SMP Debian 4.19.194-3 (2021-07-18) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Oct 23 12:32:01 2021 from 79.95.87.35
level1@fweefwoplinux:~$ ls -lRa
.:
total 24
dr-x------ 3 level1 level1 4096 Oct 18 00:17 .
drwxr-xr-x 15 root root 4096 Oct 18 00:12 ..
-r--r--r-- 1 level1 level1 220 Apr 18 2019 .bash_logout
-r--r--r-- 1 level1 level1 3526 Apr 18 2019 .bashrc
-r--r--r-- 1 level1 level1 807 Apr 18 2019 .profile
dr-xr-xr-x 2 root root 4096 Oct 18 00:18 subdir
./subdir:
total 8
dr-xr-xr-x 2 root root 4096 Oct 18 00:18 .
dr-x------ 3 level1 level1 4096 Oct 18 00:17 ..
-r--r--r-- 1 root root 0 Oct 18 00:18 fwopCTF{level_2_l46h3}
fwopCTF{level_2_l46h3}
$ ssh level2@linux.fweefwop.club
level2@linux.fweefwop.club's password:
Linux fweefwoplinux 4.19.0-17-cloud-amd64 #1 SMP Debian 4.19.194-3 (2021-07-18) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Oct 23 12:33:49 2021 from 79.95.87.35
level2@fweefwoplinux:~$ ls -lRa
.:
total 24
dr-x------ 2 level2 level2 4096 Oct 18 00:19 .
drwxr-xr-x 15 root root 4096 Oct 18 00:12 ..
-r--r--r-- 1 level2 level2 220 Apr 18 2019 .bash_logout
-r--r--r-- 1 level2 level2 3526 Apr 18 2019 .bashrc
-r--r--r-- 1 level2 level2 807 Apr 18 2019 .profile
-r--r--r-- 1 root root 23 Oct 18 00:19 flag.txt
level2@fweefwoplinux:~$ cat flag.txt
fwopCTF{level_3_ti8fx}
fwopCTF{level_3_ti8fx}
$ ssh level3@linux.fweefwop.club
level3@linux.fweefwop.club's password:
Linux fweefwoplinux 4.19.0-17-cloud-amd64 #1 SMP Debian 4.19.194-3 (2021-07-18) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Oct 23 12:34:45 2021 from 79.95.87.35
level3@fweefwoplinux:~$ ls -lRa
.:
total 20
dr-x------ 2 level3 level3 4096 Oct 18 00:20 .
drwxr-xr-x 15 root root 4096 Oct 18 00:12 ..
-r--r--r-- 1 level3 level3 220 Apr 18 2019 .bash_logout
-r--r--r-- 1 level3 level3 3564 Oct 18 00:20 .bashrc
-r--r--r-- 1 level3 level3 807 Apr 18 2019 .profile
level3@fweefwoplinux:~$ env | grep fwop
FLAG=fwopCTF{level_4_nmc4e}
fwopCTF{level_4_nmc4e}
$ ssh level4@linux.fweefwop.club
level4@linux.fweefwop.club's password:
Linux fweefwoplinux 4.19.0-17-cloud-amd64 #1 SMP Debian 4.19.194-3 (2021-07-18) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Oct 23 12:43:50 2021 from 79.95.87.35
level4@fweefwoplinux:~$ ls -lRa
.:
total 24
dr-x------ 3 level4 level4 4096 Oct 18 00:24 .
drwxr-xr-x 15 root root 4096 Oct 18 00:12 ..
-r--r--r-- 1 level4 level4 220 Apr 18 2019 .bash_logout
-r--r--r-- 1 level4 level4 3526 Apr 18 2019 .bashrc
-r--r--r-- 1 level4 level4 807 Apr 18 2019 .profile
dr-xr-xr-x 3 root root 4096 Oct 18 00:25 pneumonoultramicroscopicsilicovolcanoconiosis
./pneumonoultramicroscopicsilicovolcanoconiosis:
total 12
dr-xr-xr-x 3 root root 4096 Oct 18 00:25 .
dr-x------ 3 level4 level4 4096 Oct 18 00:24 ..
dr-xr-xr-x 3 root root 4096 Oct 18 00:27 hippopotomonstrosesquippedaliophobia
./pneumonoultramicroscopicsilicovolcanoconiosis/hippopotomonstrosesquippedaliophobia:
total 12
dr-xr-xr-x 3 root root 4096 Oct 18 00:27 .
dr-xr-xr-x 3 root root 4096 Oct 18 00:25 ..
dr-xr-xr-x 2 root root 4096 Oct 18 00:27 really_long_name_so_you_dont_type_it_but_not_long_enough_that_it_obscures_your_screen_and_stuff_lol_I_dont_know_what_to_put_here
./pneumonoultramicroscopicsilicovolcanoconiosis/hippopotomonstrosesquippedaliophobia/really_long_name_so_you_dont_type_it_but_not_long_enough_that_it_obscures_your_screen_and_stuff_lol_I_dont_know_what_to_put_here:
total 12
dr-xr-xr-x 2 root root 4096 Oct 18 00:27 .
dr-xr-xr-x 3 root root 4096 Oct 18 00:27 ..
-r--r--r-- 1 root root 21 Oct 18 00:27 flag
level4@fweefwoplinux:~$ cat ./pneumonoultramicroscopicsilicovolcanoconiosis/hippopotomonstrosesquippedaliophobia/really_long_name_so_you_dont_type_it_but_not_long_enough_that_it_obscures_your_screen_and_stuff_lol_I_dont_know_what_to_put_here/flag
fwopCTF{level_5_4gw}
fwopCTF{level_5_4gw}
$ ssh level5@linux.fweefwop.club
level5@linux.fweefwop.club's password:
Linux fweefwoplinux 4.19.0-17-cloud-amd64 #1 SMP Debian 4.19.194-3 (2021-07-18) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Oct 23 12:45:27 2021 from 79.95.87.35
level5@fweefwoplinux:~$ ls -lRa
.:
total 1504
dr-x------ 2 level5 level5 4096 Oct 18 00:35 .
drwxr-xr-x 15 root root 4096 Oct 18 00:12 ..
-r--r--r-- 1 level5 level5 220 Apr 18 2019 .bash_logout
-r--r--r-- 1 level5 level5 3526 Apr 18 2019 .bashrc
-r--r--r-- 1 level5 level5 807 Apr 18 2019 .profile
-r--r--r-- 1 root root 1518096 Oct 18 00:35 flag.txt
level5@fweefwoplinux:~$ cat flag.txt | grep fwop
Urna nunc id cursus metus aliquam eleifend mi in. Magna sit amet purus gravida. Facilisi etiam dignissim diam quis enim. Quis viverra nibh cras pulvinar mattis nunc sed. fwopCTF{level_6_3bw} Viverra adipiscing at in tellus integer feugiat scelerisque. Enim diam vulputate ut pharetra sit amet. Ut tristique et egestas quis ipsum suspendisse ultrices gravida. Arcu bibendum at varius vel pharetra. Ut faucibus pulvinar elementum integer enim neque volutpat. Viverra maecenas accumsan lacus vel facilisis volutpat est velit egestas. Vitae turpis massa sed elementum. Lacinia at quis risus sed vulputate odio ut enim. Scelerisque varius morbi enim nunc faucibus. Tellus in metus vulputate eu scelerisque felis imperdiet proin fermentum. Phasellus faucibus scelerisque eleifend donec pretium vulputate sapien nec sagittis. Nec sagittis aliquam malesuada bibendum arcu vitae elementum curabitur vitae. Urna molestie at elementum eu facilisis sed. Ac tortor vitae purus faucibus. Arcu odio ut sem nulla pharetra diam sit amet nisl. In aliquam sem fringilla ut morbi tincidunt augue interdum.
fwopCTF{level_6_3bw}
$ ssh level6@linux.fweefwop.club
level6@linux.fweefwop.club's password:
Linux fweefwoplinux 4.19.0-17-cloud-amd64 #1 SMP Debian 4.19.194-3 (2021-07-18) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Oct 23 12:53:42 2021 from 79.95.87.35
level6@fweefwoplinux:~$ ls -lRa
.:
total 24
dr-x------ 2 level6 level6 4096 Oct 18 00:36 .
drwxr-xr-x 15 root root 4096 Oct 18 00:12 ..
-r--r--r-- 1 level6 level6 220 Apr 18 2019 .bash_logout
-r--r--r-- 1 level6 level6 3526 Apr 18 2019 .bashrc
-r--r--r-- 1 root root 21 Oct 18 00:36 .flag.txt
-r--r--r-- 1 level6 level6 807 Apr 18 2019 .profile
level6@fweefwoplinux:~$ cat .flag.txt
fwopCTF{level_7_82j}
fwopCTF{level_7_82j}
$ ssh level7@linux.fweefwop.club
level7@linux.fweefwop.club's password:
Linux fweefwoplinux 4.19.0-17-cloud-amd64 #1 SMP Debian 4.19.194-3 (2021-07-18) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Oct 23 12:55:06 2021 from 79.95.87.35
level7@fweefwoplinux:~$ ls -lRa
.:
total 24
dr-x------ 2 level7 level7 4096 Oct 18 00:42 .
drwxr-xr-x 15 root root 4096 Oct 18 00:12 ..
-r--r--r-- 1 level7 level7 220 Apr 18 2019 .bash_logout
-r--r--r-- 1 level7 level7 3526 Apr 18 2019 .bashrc
-r--r--r-- 1 level7 level7 807 Apr 18 2019 .profile
-r--r--r-- 1 root root 21 Oct 18 00:43 flag.png
level7@fweefwoplinux:~$ file flag.png
flag.png: ASCII text
level7@fweefwoplinux:~$ cat flag.png
fwopCTF{level_8_2b3}
fwopCTF{level_8_2b3}
$ ssh level8@linux.fweefwop.club
level8@linux.fweefwop.club's password:
Linux fweefwoplinux 4.19.0-17-cloud-amd64 #1 SMP Debian 4.19.194-3 (2021-07-18) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Oct 23 13:25:07 2021 from 90.152.192.27
level8@fweefwoplinux:~$ ls -lRa
.:
total 436
dr-x------ 2 level8 level8 4096 Oct 18 00:30 .
drwxr-xr-x 15 root root 4096 Oct 18 00:12 ..
-r--r--r-- 1 level8 level8 220 Apr 18 2019 .bash_logout
-r--r--r-- 1 level8 level8 3526 Apr 18 2019 .bashrc
-r--r--r-- 1 level8 level8 807 Apr 18 2019 .profile
-r--r--r-- 1 root root 210000 Oct 18 00:30 f1.txt
-r--r--r-- 1 root root 210021 Oct 18 00:30 f2.txt
level8@fweefwoplinux:~$ diff f1.txt f2.txt
1773a1774
> fwopCTF{level_9_c2p}
fwopCTF{level_9_c2p}
$ ssh level9@linux.fweefwop.club
level9@linux.fweefwop.club's password:
Linux fweefwoplinux 4.19.0-17-cloud-amd64 #1 SMP Debian 4.19.194-3 (2021-07-18) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Oct 23 13:29:34 2021 from 90.152.192.27
level9@fweefwoplinux:~$ ls -lRa
.:
total 24
-r--r--r-- 1 root root 22 Oct 18 01:05 -cant_touch_this
dr-x------ 2 level9 level9 4096 Oct 18 01:05 .
drwxr-xr-x 15 root root 4096 Oct 18 00:12 ..
-r--r--r-- 1 level9 level9 220 Apr 18 2019 .bash_logout
-r--r--r-- 1 level9 level9 3526 Apr 18 2019 .bashrc
-r--r--r-- 1 level9 level9 807 Apr 18 2019 .profile
level9@fweefwoplinux:~$ cat ./-cant_touch_this
fwopCTF{level_10_fqd}
fwopCTF{level_10_fqd}
$ ssh level10@linux.fweefwop.club
level10@linux.fweefwop.club's password:
Linux fweefwoplinux 4.19.0-17-cloud-amd64 #1 SMP Debian 4.19.194-3 (2021-07-18) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Oct 23 14:06:37 2021 from 37.192.231.16
level10@fweefwoplinux:~$ ls -lRa
.:
total 24
dr-x------ 2 level10 level10 4096 Oct 23 03:13 .
drwxr-xr-x 15 root root 4096 Oct 18 00:12 ..
-r--r--r-- 1 level10 level10 220 Apr 18 2019 .bash_logout
-r--r--r-- 1 level10 level10 3526 Apr 18 2019 .bashrc
-r--r--r-- 1 level10 level10 807 Apr 18 2019 .profile
-rw-r--r-- 1 root root 54 Oct 23 03:13 readme
level10@fweefwoplinux:~$ cat readme
Level 11 password is in a file named level11_flag.txt
level10@fweefwoplinux:~$ find / -name level11_flag.txt
find: ‘/lost+found’: Permission denied
find: ‘/sys/kernel/debug’: Permission denied
:
find: ‘/proc/30761/fdinfo’: Permission denied
find: ‘/proc/30761/ns’: Permission denied
/usr/local/share/man/level11_flag.txt
find: ‘/etc/ssl/private’: Permission denied
find: ‘/root’: Permission denied
find: ‘/run/chrony’: Permission denied
:
level10@fweefwoplinux:~$ cat /usr/local/share/man/level11_flag.txt
fwopCTF{level_11_87h}
fwopCTF{level_11_87h}
Simple MD5 (Crypto 100)
指定の文字列のMD5の値を答える。
$ echo -n "Happy as a Clam" | md5sum
7ca2197c58b026825c382e32621b1ce4 -
||
>|
<b>7ca2197c58b026825c382e32621b1ce4</b>
|<
* Oink (Crypto 100)
Pigpen cipher。https://www.dcode.fr/pigpen-cipherで復号する。
>|
<b>WELOVEPIGS</b>
|<
* FlipFwop (Crypto 100)
鏡文字になっているので、左右反転する。
>|
<b>fwopCTF{earth_fire_water_air}</b>
|<
* Where's the message? (Crypto 100)
意味のあるよう取り出す文字を調整しながら、アルファベット大文字だけ並べる。
>|
<b>WOWTHANKS</b>
|<
* WireBirds (Crypto 100)
https://www.gagb.org.uk/puzzles.php#gsc.tab=0にある「Birds on a Wire」を参考に復号する。
>|
<b>birdsknow</b>
|<
* More than 64 (Crypto 125)
base85デコードする。
>||
>>> import base64
>>> enc = "Ap8046W?O%DffZ(EaN9aF(KE\"GAhV?A7'P!Ebf$(Df9!
>>> base64.a85decode(enc)
b'fwopCTF{other_bases_would_work_too_not_just_64}'
fwopCTF{other_bases_would_work_too_not_just_64}
5x5 (Crypto 200)
ポリビュオスの暗号表にあてはめ、復号する。
fwopCTF{polybius_square}
Baby RSA (0) (Crypto 200)
文字列を数値化する。
from Crypto.Util.number import *
s = 'fwopCTF{I_am_learning_RSA_so_exciting}'
ans = bytes_to_long(s)
print ans
13045502302425615144883543017919348302961367754511098998678884785553997741250139993469249405
Baby RSA (1) (Crypto 150)
数値を文字列化する。
from Crypto.Util.number import *
m = 643192922209641529679217093842090563198908934967463878287741
flag = long_to_bytes(m)
print flag
fwopCTF{another_baby_rsa}
Baby RSA (2) (Crypto 100)
p * qを求める。
p = 194522226411154500868209046072773892801
q = 288543888189520095825105581859098503663
n = p * q
print n
56128199547956677238767298622332803823913995062683233044001500290070667830063
Baby RSA (3) (Crypto 100)
(p - 1) * (q - 1)を求める。
p = 194522226411154500868209046072773892801
q = 288543888189520095825105581859098503663
phi = (p - 1) * (q - 1)
print phi
56128199547956677238767298622332803823430928948082558447308185662138795433600
Baby RSA (4) (Crypto 200)
RSA暗号を行う。
from Crypto.Util.number import *
p = 194522226411154500868209046072773892801
q = 288543888189520095825105581859098503663
e = 65537
s = 'fwop{baby_rsa}'
m = bytes_to_long(s)
c = pow(m, e, p * q)
print c
16832067193038570664627710532871887598013604871431045374089410572330773390687
Baby RSA (5) (Crypto 100)
inverseを使ってdを算出する。
from Crypto.Util.number import *
p = 194522226411154500868209046072773892801
q = 288543888189520095825105581859098503663
e = 65537
phi = (p - 1) * (q - 1)
d = inverse(e, phi)
print d
39365191632547732007914614856903809984286421688048990897845086680417895132673
Baby RSA (6) (Crypto 200)
RSA暗号だが、p, qがわかっているので、通常通り復号する。
from Crypto.Util.number import *
p = 194522226411154500868209046072773892801
q = 288543888189520095825105581859098503663
e = 65537
enc = 5052002876272730069345319419734444235143011589416753056749825264763216780757
phi = (p - 1) * (q - 1)
d = inverse(e, phi)
m = pow(enc, d, p * q)
flag = long_to_bytes(m)
print flag
fwopCTF{how_many_more_baby_rsa?}
2B, or not 2B! (Crypto 200)
hexデコードする。
>>> s = '2b2b2b2b2b2b2b2b2b2b5b3e2b3e2b2b2b3e2b2b2b2b2b2b2b3e2b2b2b2b2b2b2b2b2b2b3c3c3c3c2d5d3e3e3e3e2b2b2e2b2b2b2b2b2b2b2b2b2b2b2b2b2b2b2b2b2e2d2d2d2d2d2d2d2d2e2b2e3c2d2d2d2e2b2b2b2b2b2b2b2b2b2b2b2b2b2b2b2b2b2e2d2d2d2d2d2d2d2d2d2d2d2d2d2d2e3e2b2b2b2b2b2b2b2b2b2b2b2e3c2b2b2b2b2b2b2b2b2b2b2b2b2b2e3e2d2d2d2d2d2d2d2d2d2d2d2d2e2d2d2e2d2d2d2d2d2d2d2d2e2b2b2b2b2b2b2b2b2b2b2b2b2b2b2b2e2d2d2d2d2d2d2d2d2d2d2d2d2e2b2e2b2b2b2b2b2e2d2d2d2d2d2d2d2e2d2d2d2d2d2d2d2d2e2b2b2b2b2b2b2b2b2b2b2e2b2b2b2b2b2b2b2b2b2b2e3c2b2b2b2b2b2b2b2b2b2b2b2b2e3e2d2e2d2d2d2e2b2b2b2b2b2e2e3c2b2b2b2b2b2b2e3e2d2d2d2d2d2d2e3c2d2d2d2d2d2d2e3e2d2d2d2d2d2e2b2b2b2b2b2e3c2e3e2b2b2b2b2b2b2e3c2b2b2b2b2b2b2b2b2b2e2d2d2d2e2d2d2d2d2d2d2e3e2d2e2b2e3c2b2b2e3e2e3c2b2b2b2b2e2d2d2d2d2d2d2e3e2d2d2d2d2d2e3c2b2b2b2b2b2b2b2e2d2d2d2d2d2d2d2e2d2d2d2d2d2d2d2d2d2d2d2d2d2d2d2d2d2d2d2d2d2d2d2d2d2d2d2e3e2d2d2d2d2d2d2d2d2d2d2e2b2b2b2b2b2b2b2b2b2e2d2e2d2d2d2d2d2d2d2d2d2d2d2d2e2b2b2b2b2b2b2b2b2b2b2b2b2b2b2b2b2b2e2d2d2d2d2d2d2d2e2b2b2b2b2b2b2b2b2b2b2b2b2b2b2b2b2b2b2e'
>>> s.decode('hex')
'++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>>++.+++++++++++++++++.--------.+.<---.+++++++++++++++++.--------------.>+++++++++++.<+++++++++++++.>------------.--.--------.+++++++++++++++.------------.+.+++++.-------.--------.++++++++++.++++++++++.<++++++++++++.>-.---.+++++..<++++++.>------.<------.>-----.+++++.<.>++++++.<+++++++++.---.------.>-.+.<++.>.<++++.------.>-----.<+++++++.-------.---------------------------.>----------.+++++++++.-.------------.+++++++++++++++++.-------.++++++++++++++++++.'Brainf*ck言語のようだ。https://sange.fi/esoteric/brainfuck/impl/interp/i.htmlで実行する。
fwopCTF{Something_is_rotten_in_the_state_of_Denmark}
Silly Secret Sharing (SSS) (Crypto 200)
2人でSSSを使っているので、一次方程式のグラフを使う。方程式を解き、その切片がPINになる。
from sympy import *
p1 = (20, 161013)
p2 = (10, 122673)
a = symbols('a')
b = symbols('b')
eq1 = Eq(a * p1[0] + b, p1[1])
eq2 = Eq(a * p2[0] + b, p2[1])
sol = solve ([eq1, eq2], [a, b])
pin = sol[b]
print pin
84333
Unbreakable (Crypto 250)
$ echo V3Z4bHd2IGdzdiB1bG9vbGRybXQgaGdpcm10CkVUc29SVjFWTUhZbEJDTWxSU0FzeVNFb1JUOW5SU0lsQUhZbnlUVW1SVG9hUldRc04yRXFNcUIwTFd0NE1Xd29NYXA0QmFSNUFHQXJNR1pkQkdVckIyTjJPWFkzekNJbFJUQTN5M1lXRVZBN3VIWXN4bjkxeW5KdHpDSmY= | base64 -d
Wvxlwv gsv ulooldrmt hgirmt
ETsoRV1VMHYlBCMlRSAsySEoRT9nRSIlAHYnyTUmRToaRWQsN2EqMqB0LWt4MWwoMap4BaR5AGArMGZdBGUrB2N2OXY3zCIlRTA3y3YWEVA7uHYsxn91ynJtzCJf
Atbash cipher。https://www.geocachingtoolbox.com/index.php?lang=en&page=atbashCipherで復号する。
Decode the following string
VGhlIE1ENSBoYXNoIHZhbHVlIG9mIHRoZSBmbGFnIGlzIDJhM2VjNjY0ODg4NDdlNzk4YzI5ZTZiNTAwYTFiY2M2LCB3aXRoIGZ3b3BDVEZ7fSBhcm91bmQgaXQu
$ echo VGhlIE1ENSBoYXNoIHZhbHVlIG9mIHRoZSBmbGFnIGlzIDJhM2VjNjY0ODg4NDdlNzk4YzI5ZTZiNTAwYTFiY2M2LCB3aXRoIGZ3b3BDVEZ7fSBhcm91bmQgaXQu | base64 -d
The MD5 hash value of the flag is 2a3ec66488847e798c29e6b500a1bcc6, with fwopCTF{} around it.
このmd5をCrackStationでクラックする。
antidisestablishmentarianism
fwopCTF{antidisestablishmentarianism}
My mind is all blanks (Crypto 250)
"\x09"と"\x20"の文字だけがある。"\x09"を"0"、"\x20"を"1"に置換し、デコードする。ASCIIコードの羅列になるので、さらにデコードする。
with open('blanks.txt', 'r') as f:
data = f.read()
data = data.replace('\x09', '0')
data = data.replace('\x20', '1')
codes = ''
for i in range(0, len(data), 8):
codes += chr(int(data[i:i+8], 2))
codes = map(int, codes.split(','))
flag = ''
for code in codes:
flag += chr(code)
print flag
fwopCTF{tab_tap_tab_top}
This is just ridiculous! (Crypto 300)
CyberChefで以下のレシピで復号する。
・From Base64
・From Binary
・From Base64
・From Hex
・From Base64
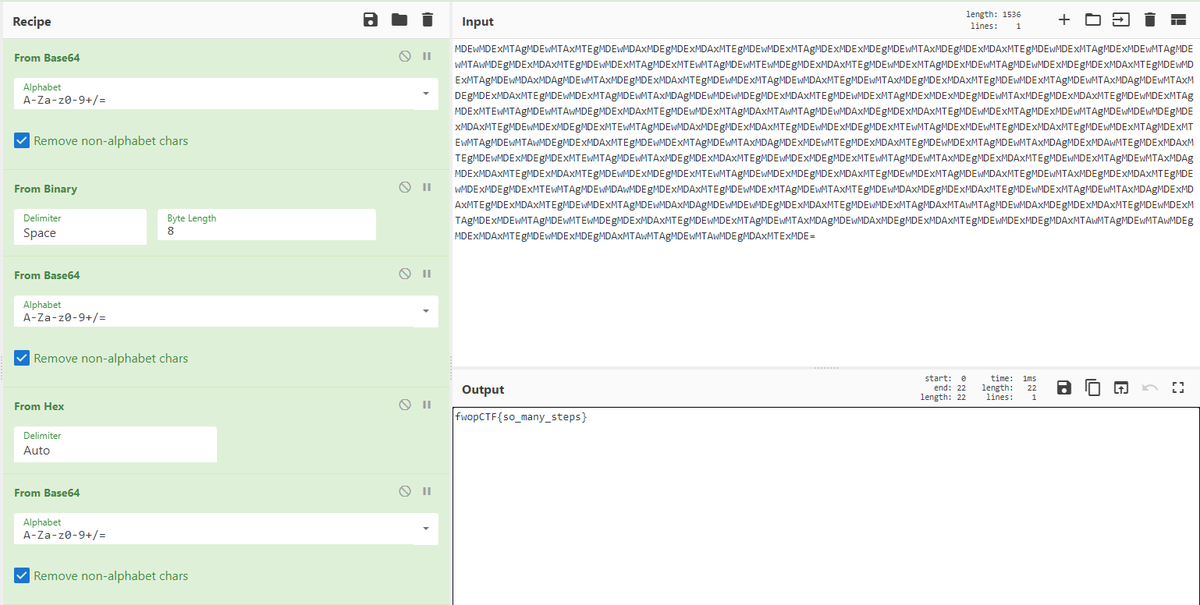
fwopCTF{so_many_steps}
Borg (Crypto 300)
keyは2バイトのXOR暗号と推測できる。
enc = [0xcc, 0xdd, 0xc5, 0xda, 0xe9, 0xfe, 0xec, 0xd1, 0xd8, 0xcf, 0xd9, 0xc3,
0xd9, 0xde, 0xcb, 0xc4, 0xc9, 0xcf, 0xf5, 0xc3, 0xd9, 0xf5, 0xcc, 0xdf,
0xde, 0xc3, 0xc6, 0xcf, 0xd7]
flag_head = 'fwop'
key = []
for i in range(len(flag_head)):
key.append(ord(flag_head[i]) ^ enc[i])
assert key[:2] == key[2:]
key = key[:2]
flag = ''
for i in range(len(enc)):
flag += chr(enc[i] ^ key[i%len(key)])
print flag
fwopCTF{resistance_is_futile}
Toddler RSA (Crypto 300)
nをfactordbで素因数分解する。
n = 6072510988286929264894086362835077173625040072601309544494353950350290130736379974160352667353769493236336930449438771170009858935018137670526822423479179 * 7997416035266735376949323633693044943877117000985893501813767052682242347917960725109882869292648940863628350771736250400726013095444943539503502901307363
あとはそのまま復号する。
from Crypto.Util.number import *
n = 48564396752059338791464352725210493148212425902751190745668164451763507023284970474595680869078726765719920168392505794415687815488076204724659643390252172928332322944711949999326843460702414647825442748821062427474599006915155109396213406624079900714394311217571510958430682853948004734434233860146109894977
e = 31337
enc = 41150528980309124566759211353926954600326212451943427970714522842710817302495300068872479882906452508829057279560763667181476082807039520594933172924095664670761580311804814234298908677404942630507776935683606361298186524479302515125123817250737921124161083117345688744816192619093876226182512278538279004036
p = 6072510988286929264894086362835077173625040072601309544494353950350290130736379974160352667353769493236336930449438771170009858935018137670526822423479179
q = 7997416035266735376949323633693044943877117000985893501813767052682242347917960725109882869292648940863628350771736250400726013095444943539503502901307363
phi = (p - 1) * (q - 1)
d = inverse(e, phi)
m = pow(enc, d, n)
flag = long_to_bytes(m)
print flag
fwopCTF{cute_toddler_rsa}
Open Secret (Crypto 300)
A = pow(g, a, p)
B = pow(g, b, p)
bの秘密鍵がわかっているので、共有鍵を以下で計算できる。
key = pow(g, a * b, p) = pow(pow(g, a, p), b, p) = pow(A, b, p)
あとはXORで復号する。
from Crypto.Util.number import *
enc = 'T6ZBVGqFaF9gjkhLXL9Ke125S3tIvUdBR45GTVqOQEVEtHFNWo5eRVy9Uw=='.decode('base64')
p = 824717393
g = 150357959
A = 734947628
b = 845023462
B = pow(g, b, p)
key = pow(A, b, p)
s_key = long_to_bytes(key)
flag = ''
for i in range(len(enc)):
flag += chr(ord(enc[i]) ^ ord(s_key[i%len(s_key)]))
print flag
fwopCTF{I_found_the_alien_his_name_is_paul}
Pretty Safe Password (Crypto 300)
ブルートフォースでパスワードを求める。
import hashlib
with open('10k-most-common.txt', 'r') as f:
words = f.read().splitlines()
for word in words:
password = 'fwopCTF{%s}' % word
h = hashlib.md5(password).hexdigest()
if h == '3777de3a24c77814c1e4e27aeb9e40e3':
print password
break
fwopCTF{pa55word}
Home Run (Crypto 350)
CyberChefで以下のレシピで復号する。
・From Base64
・From Base64
・From Base64
・From Binary
・From Hex
・From Base32
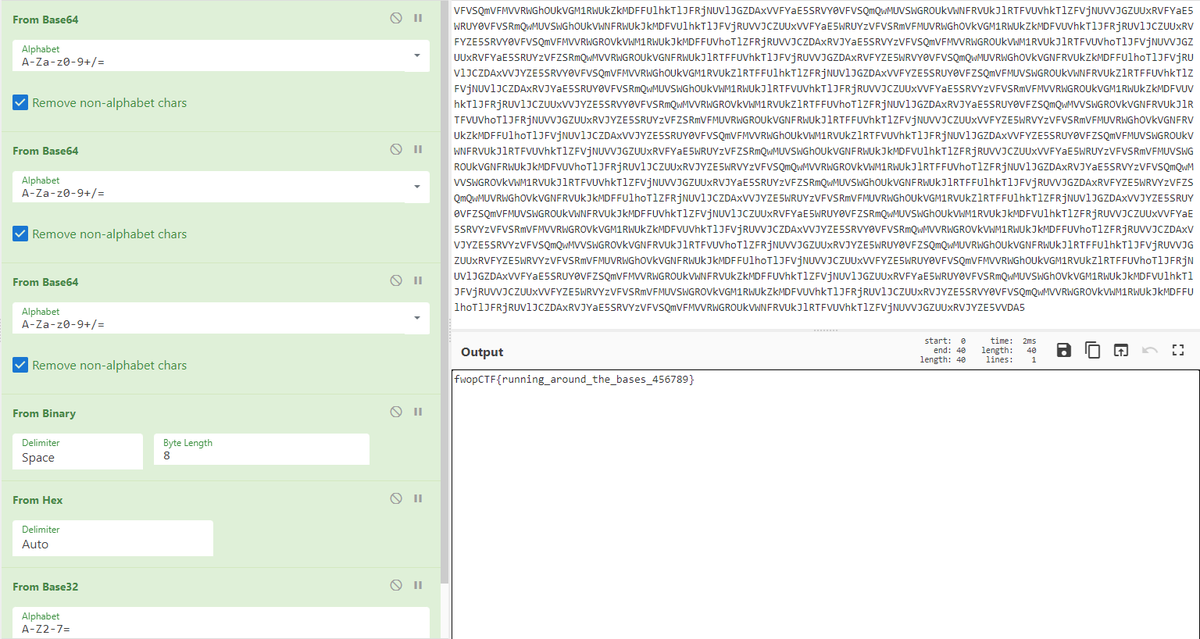
fwopCTF{running_around_the_bases_456789}
Elementary RSA (Crypto 350)
n, qがわかっているので、pを算出できる。あとはそのまま復号する。
from Crypto.Util.number import *
c = 7547565125898378215297051739440246888835869128178814602128398471744328137846645196352789690502829388481328147506940018807183449257834243707849773598414393305253794845257619586242775698697470314118958662932787038546427248055484396055575105135110971290111917998933205130176836472894218594817189395314880103599436146900262227720584244587872516862458558944038921270858082562381938645818571307807059350434544612575270526939881886666213772988313967785602967403463328683642452412570738638011516486964398202827383201545380219462136633609360170379918362441554815623555045825134255750316711554991895782546314094842951837239221
e = 65537
n = 13715280123196571296040497170215424559841118434271081143085393254503221402455218866367322935884205486745414412072737147619005701422821619176312036264040746835557434946118113454705949958288089469537242690516793314691009138099296393081195700382103932212016949324612763350891225015815072676716589951974500241683728451552619937957018532227780090226646421633572025828452979286761778535053778685371789594887586906300906069495398868677875457680655416855327598433514199221642516967512865226196097662282605095102549022089757838743887028753811567234292303888034615388451343532612361239809487469031081253702053913483627342967513
q = 138295817899027125589939386105258578479159740431881274316292285949477631403445673197617716066873262776020799538878278844875145015704122766147923557098420440559040775768532377541317308499486891858654315671171927898037446605115409768580966408482758441823375862061789309173422687582436899562827562898907601960829
assert n % q == 0
p = n // q
phi = (p - 1) * (q - 1)
d = inverse(e, phi)
m = pow(c, d, n)
flag = long_to_bytes(m)
print flag
fwopCT{don't_be_so_clumsy}フラグの形式を修正する。
fwopCTF{don't_be_so_clumsy}
Kinder RSA (Crypto 400)
RSAのパラメータがそろっているので、そのまま復号する。
from Crypto.Util.number import *
p = 117025919863324186220155912379493510806938956278523335096778026828600895382729413686432125512416987242961255888204400422166767227569280578840187401896714137293001805171341988321852662908122640026581641142465496641866004143100724149516317767459196996302881487013468733667218264219949378827091463411801040433333
e = 65537
c = 3176947916522045759269309860247477806969078544628032431086054916430409561492643390296727934584958799568295039721459221273731800678329151618879869923278910592515839775128584789876977122269445555178438315335177456488472866165828523483080654047393581475909777710523063691395238952705004953255824614927142500947607632610806109942257461826838758244571120945151163127971358262552910600456763503073429250752505495874926777120685874043361508768889445750979867041183999386035611654705651426768594305162794625276466933203875604190503709758422736145157145383125237582611020912918611460533424111536366894528559932701001420239552
n = 10682780633991969177677032196019939027985208229946310919966442519465032181529225488298110788841863113629067354740714072936547257627785850653093685942691560550065001809296374399373377762142325828132422097371522127911728321208614509277335352830189983100178132982012599369846533458595399722731354088854256306846226824731309968110658509633139142049891064431405878186536015671444740708232423766875328640331661803993022425821117080195996399180194864792793387232822578898138983860268605248897408399776140269518083235613918473829364123401722919836036448967473751808918526526887166533489699341809254472381445194313968211679501
d = 8349870118806759862772265655143222556854025841570407203187222760571833826675535585059900898094579214728305769971055714881282836748452480273810581235246886326458027033297324848679391425694502960863074628650323038928823157207551127420106252173985411054925078383258241950659759775646571414573654778240677469493374709546552017058197814263099082949885338486829565261098097424038912450740413892281133896808838467269433631566299466640664843204006072812868977520672537372503857475581013879592069870672135240300086821446969927789617435024923930106366843309026147286983416006068948362159060850750634615509439576603194180447073
q = 91285594221079416032103777163267879510959473929712713487338945167858596955609331062421703786334194408687389318748343117328864181792085064377910816336971021816498260521315839846898184613459752604302179787801085385679518199989894907975205676468500840003987942953430961153503606127238899378811680500145951061497
t = 10682780633991969177677032196019939027985208229946310919966442519465032181529225488298110788841863113629067354740714072936547257627785850653093685942691560550065001809296374399373377762142325828132422097371522127911728321208614509277335352830189983100178132982012599369846533458595399722731354088854256306846018513217225564508406249943596380659573166001197642137951898699448281215894085022126474811032910622341373780614164336656500767770833499149575289014588893739029483794575947420728657552254557876887199414683651891801818601058632300778544925523546053972611657096920266838668977471462066194175542050402021220184672
assert n == p * q
assert t == (p - 1) * (q - 1)
assert d == inverse(e, t)
m = pow(c, d, n)
flag = long_to_bytes(m)
print flag
fwopCTF{oh_no_my_information}
Strange RSA (Crypto 400)
RSA暗号で、n, p, q, e, cが与えられているが、n = p * qとはなっていない。nはp、qともに割り切れるので、割ってみると、その数値は素数になった。この素数をrとすると、以下のようになるので、あとはそのまま復号する。
n = p * q * r
phi = (p - 1) * (q - 1) * (r - 1)
from Crypto.Util.number import *
n = 7951018409693161668167285098819306759801615467749983772377532762274564323674475529781135819956076874943220398570628206016160240882619874330243093244936395110045993507712409313429053491882557640392921080389040202564944368311332322835084748219968985945494232530915619964225016803746552927248389191728978163526848645974605789560442463273013903681542284658299342143
p = 1929116635275264735053674741049427216734778196597952692885273974756157874848524489523506992386257196915978454424769273897
q = 1903374449504601072452320486035709413287524054085898117310656797189766004182623359564618504846582607657952100194953437513
e = 65537
c = 5966972166891478943697533397002317526062125536151178353483752855912660840768728401988233413928558098251299119103372377488247940263788187179216261221551423070667612264065068718276490178352621443926803409497199336389072678702084464080895190403103597610490385133200289793164066702537822343346786026894342086902097286424450736331498175097265162507503062204219321005
assert n % p == 0
assert n % q == 0
r = n // (p * q)
assert isPrime(r)
phi = (p - 1) * (q - 1) * (r - 1)
d = inverse(e, phi)
m = pow(c, d, n)
flag = long_to_bytes(m)
print flag
fwopCTF{triple_primes_also_work}
Teenager RSA (Crypto 500)
1文字ずつRSA暗号を行っていると推測できる。またp, q, eは不明だが、20より小さいので"fwopCTF{"で始まることを前提にブルートフォースで復号する。
from Crypto.Util.number import *
enc = [119, 37, 45, 18, 89, 72, 60, 7, 80, 21, 59, 4, 4, 17, 33, 39, 21, 32,
62, 49, 80, 17, 59, 49, 62, 17, 37, 62, 59, 68, 5]
flag_head = 'fwopCTF{'
found = False
for p in range(1, 20):
for q in range(1, 20):
for e in range(1, 20):
success = True
for i in range(len(flag_head)):
m = ord(flag_head[i])
if pow(m, e, p * q) != enc[i]:
success = False
break
if success:
found = True
break
if found:
break
if found:
break
print '[+] p =', p
print '[+] q =', q
print '[+] e =', e
phi = (p - 1) * (q - 1)
d = inverse(e, phi)
flag = ''
for c in enc:
m = pow(c, d, p * q)
flag += chr(m)
print '[*] flag =', flag
実行結果は以下の通り。
[+] p = 11
[+] q = 13
[+] e = 7
[*] flag = fwopCTF{small_numbers_are_weak}
fwopCTF{small_numbers_are_weak}
Thanos RSA (Crypto 500)
eが小さいので、Low Public-Exponent Attackで復号する。
from Crypto.Util.number import *
import gmpy
n = 90853943628322295026593682475987617060873593704720419107522455730118510052263265463293746646770270649687914442326502298395536584315638883283598508714600968672217889495196802078585067900709511094279209391102167066735509213687150809291297894333497926049791571469926970525133534853823359619169977902549379766690271029677550623981924039537745336236460806578804468603462430628647190394537926168276717097453855467142322886378913606046349505735904238841871750986024415032881423400763965392179016644748395748894328459546597234450779143514757379951569086179358016591843479108891552906656123595991984678135372139
e = 3
c = 353690381812046953967046705467201123771968703796985157143856239677213620452330219172911759040152594421289421265846324253121362172623915294111963396504119782165935747889254103399163563246766329595499703665701197666661
m = gmpy.root(c, e)[0]
flag = long_to_bytes(m)
print flag
fwopCTF{small_exponent_is_bad}
Super Safe Password (Crypto 500)
ブルートフォースでパスワードを求める。
import hashlib
with open('10k-most-common.txt', 'r') as f:
words = f.read().splitlines()
found = False
for word in words:
for word2 in words:
password = 'fwopCTF{%s%s}' % (word, word2)
h = hashlib.md5(password).hexdigest()
if h == 'f4552088fd3266916b4fb22757b668cc':
found = True
print password
break
if found:
break
fwopCTF{cyprusdante1}
In Front Of Your Eyes (Web 100)
HTMLソースを見たら、フラグが見つかった。
fwopCTF{Wolfy_The_Wolf}
Robot Invasion (Web 100)
https://web.fweefwop.club/robots.txtにアクセスすると、こう書いてある。
User-agent: *
Disallow: /
Disallow: /totally_evil_plan
https://web.fweefwop.club/totally_evil_planにアクセスすると、フラグが見つかった。
Step 1: Hire engineers to build a robot army that follows my every command
Step 2: Command those robots to obliterate the engineers because I am broke and cannot afford to pay them
Step 3: ???
Step 4: World Domination
fwopCTF{k1ller_r0bots_wilL_rUl3_th3_W0rld!!1}
fwopCTF{k1ller_r0bots_wilL_rUl3_th3_W0rld!!1}
Marq-weeeeeee! (Web 100)
フラグっぽい文字列がたくさん流れてくるが、フラグ形式としてはおかしいものがほとんど。"fwopCTF{"で検索すると一つだけヒットした。
fwopCTF{t3f0n00}
No Inspector (Web 100)
HTMLソースにjsのリンクがある。https://web.fweefwop.club/boring_script.jsにアクセスすると、こう書いてあった。
console.log("Oh, okay, so it seems like you do actually know your stuff.");
console.log("You can join, but just promise me you won't discuss this with anyone. Don't want my parents finding out.");
console.log("fwopCTF{funky_0n_4_fr1day_n1ght}");
fwopCTF{funky_0n_4_fr1day_n1ght}
Complete me (Web 200)
SQLの条件を記述する際の句を答えればよい。
where
Cookies (Web 250)
CookieのUsernameキーには"user"が設定されている。[Get Cookies!]をクリックすると、「Sorry, only COOKIE MONSTER has cookies!」と表示される。
CookieのUsernameキーに"COOKIE MONSTER"と設定し、[Get Cookies!]をクリックしてみると、フラグが表示された。
fwopCTF{Nom_nom_cookies}
client side login (Web 300)
ユーザ名を入力する画面。HTMLソースを見ると、以下のように書かれている。
<script>
function verify()
{
var uname = document.getElementById("input");
if(uname.value.length == 10 && uname.value.substring(1, 4) == "bef" && uname.value.charCodeAt(8) + 20 == 117){
document.getElementById("flag").innerHTML = document.getElementById("text").innerHTML.substring(1080, 1100);
}else{
alert("nay");
}
}
</script>
これを満たすユーザ名を指定すれば良さそう。「abefaaaaaa」を入力すると、フラグが表示された。
fwopCTF{SFOVF5TENW}
weird requests huh (Web 400)
PUTメソッドでアクセスしてみる。
$ curl -X PUT https://web.fweefwop.club/requests.php
fwopCTF{what_does_put_even_do??}
<html>
<head>
</head>
<body>
<center><p>i love PUTting people down </p>
<img src="dino.jpg" />
</center>
</body>
</html>
fwopCTF{what_does_put_even_do??}
53Cr37 8r0W53r (Web 400)
HTMLソースを見るとこう書いてある。
Sorry, only our secret agents on our secret browser can access this site. </p>
UserAgentに"A3SECRET"を指定してアクセスする。
$ curl -A "A3SECRET" https://web.fweefwop.club/agent.php
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1">
<title>secret agent landing page</title>
<link href="https://cdn.jsdelivr.net/npm/bootstrap@5.1.3/dist/css/bootstrap.min.css" rel="stylesheet" integrity="sha384-1BmE4kWBq78iYhFldvKuhfTAU6auU8tT94WrHftjDbrCEXSU1oBoqyl2QvZ6jIW3" crossorigin="anonymous">
<link rel="stylesheet" href="agent.css"/>
</head>
<body class="p-2 mb-1 text-white ">
<h1 class="text-center">Secret Agent Landing Page</h1>
<br />
<p class="text-center">
fwopCTF{secret_browser_007} </p>
<!-- Agent 014, you will need to reinstall the A3SECRET browser again. We had to wipe your computer because there were government secrets on it. -->
</body>
</html>
fwopCTF{secret_browser_007}
KevinSay (Web 400)
OSコマンドインジェクションを行う。
■`ls`を入力
flag193290.txt
■`cat flag193290.txt`を入力
fwopCTF{C0MM4ND1NDJ3C710N11}
fwopCTF{C0MM4ND1NDJ3C710N11}
SQLI (Web 500)
以下でログインすると、フラグが表示された。
Username: ' or 1=1 #
Password: a
fwopCTF{Leaked_data_123}
上記がブラックリストになっている。以下でログインしてみると、フラグが表示された。
Username: a
Password: ' union select 1, 'admin', 'pass
fwopCTF{f1lt3rs_not_good_3n0ugh}
Reversing Python 1 (Reverse 100)
Pythonコードが添付されている。そのままフラグ文字列と比較している。
fwopCTF{no_python_required}
Reversing Python 2 (Reverse 150)
Pythonコードが添付されている。var4のフラグ文字列と比較している。
fwopCTF{perhaps_this_is_the_flag}
Reversing Python 3 (Reverse 175)
Pythonコードが添付されている。var3のフラグ文字列と比較している。var3に複数回別の文字列が設定されているので、最後に設定された文字列がフラグになる。
fwopCTF{see_seesaw_sheshore_see_sheshore_seasells_shells}
Reversing Python 3 Bonus (Reverse 250)
Pythonコードが添付されている。kaq8hとnw91の値を結合し、fwopCTF{}で囲ったものがフラグ。上にさかのぼって変数を検索する。
kaq8h = "a505d061c2baf118fce231d8bfc7c1cb"
nw91 = "ad34ccf7f2ed2c4b8b8c675c235fd744"
fwopCTF{a505d061c2baf118fce231d8bfc7c1cbad34ccf7f2ed2c4b8b8c675c235fd744}
Reversing Python 4 (Reverse 250)
Pythonコードが添付されている。判定直前にcorrectflagを出力させる。
var1 = 15
var2 = 4
var3 = 9
if var1 < var3:
var2 = var1 + var3
elif var3 > var2:
var1 = (var1 * var2) - var2
else:
var3 = var2 * var1
if var1 - var2 * var3 >= 10:
var1 = 15 - var3
var3 = var1 * var2
else:
var2 = var1 / var2
var3 = var3 * 2
if var1 + var2 > var3:
if var2 + 2 != var1:
correctflag = "fwopCTF{else_elif_if_elif_else_else}"
elif var3 - var1 >= var2 * var2:
correctflag = "fwopCTF{else_if_then_then_else_elif}"
elif var3 + var1 + var2 <= var3 + var1 * var2:
correctflag = "fwopCTF{then_else_else_then_if_if}"
var3 = (var3 * -1) + var1 + var2
if var3 + var2 + var1 * 2 >= 0:
if var3 == var2 * -2:
correctflag = "fwopCTF{else_then_if_then_elif_elif}"
elif var2 * var1 - var3 == 3 * var1 + 5 * var2:
correctflag = "fwopCTF{then_if_then_else_if_if}"
else:
correctflag = "fwopCTF{elif_if_if_then_elif_elif}"
print(correctflag)
fwopCTF{then_if_then_else_if_if}
Reversing Python 5 (Reverse 275)
Pythonコードが添付されている。判定直前にcorrectflagを出力させる。
correctflag = "deoxyribonucleic_acid"
correctflag = correctflag[0:4] + correctflag[7:16] + correctflag[5:2:-1]
correctflag = correctflag[4:-4] + correctflag[3*4:-1] + correctflag[-1:0:-2]
print(correctflag)
bonucleicryxriluoxe
fwopCTF{bonucleicryxriluoxe}
Reversing Python 6 (Reverse 300)
Pythonコードが添付されている。判定直前にcorrectflagを出力させる。
alphabet = "abcdefghijklmnopqrstuvwxyz{}_ABCDEFGHIJKLMNOPQRSTUVWXYZ"
code = [5, 22, 14, 15, 31, 48, 34, 26, 0, 11, 18, 14, 28, 2, 17, 24, 15, 19, 14, 28, 11, 14, 11, 27]
correctflag = ""
for currentNum in code:
correctflag = correctflag + alphabet[currentNum]
print(correctflag)
fwopCTF{also_crypto_lol}
Reversing Python 7 (Reverse 350)
スクリプトの処理概要は以下の通り。
・フラグの長さは20であるかをチェック
・フラグの後半8バイトを前半12バイト入れ替え
・semicolonpos: ;のインデックス
・enteredFlag = enteredFlag[0:semicolonpos] + "o_dddduel}"
・enteredFlag == "fwopCTF{its_time_to_dddduel}"であるかをチェック入れ替えをして、qが入っている必要があることを考慮する。
its_time_t;qfwopCTF{
Fwop Door (Reverse 500)
Pythonコードが添付されている。フラグの各文字について条件がたくさんあるので、z3で解く。
from z3 import *
n = [Int('n[%d]' % i) for i in range(60)]
s = Solver()
s.add(n[9] + n[32] + n[26] == 337)
s.add(n[47] + n[14] + n[58] == 329)
s.add(n[56] + n[32] + n[19] == 316)
s.add(n[32] + n[6] + n[51] == 304)
s.add(n[43] + n[14] + n[44] == 318)
s.add(n[55] + n[2] + n[50] == 313)
s.add(n[36] + n[50] + n[35] == 311)
s.add(n[52] + n[42] + n[55] == 311)
s.add(n[44] + n[9] + n[22] == 335)
s.add(n[57] + n[27] + n[32] == 344)
s.add(n[8] + n[33] + n[16] == 322)
s.add(n[38] + n[6] + n[26] == 273)
s.add(n[53] + n[27] + n[2] == 327)
s.add(n[15] + n[35] + n[32] == 328)
s.add(n[17] + n[15] + n[21] == 308)
s.add(n[28] + n[52] + n[22] == 326)
s.add(n[12] + n[53] + n[48] == 317)
s.add(n[34] + n[50] + n[6] == 279)
s.add(n[22] + n[32] + n[47] == 347)
s.add(n[30] + n[32] + n[38] == 333)
s.add(n[48] + n[7] + n[59] == 359)
s.add(n[40] + n[15] + n[31] == 299)
s.add(n[20] + n[30] + n[15] == 304)
s.add(n[19] + n[7] + n[13] == 321)
s.add(n[54] + n[36] + n[56] == 306)
s.add(n[37] + n[10] + n[5] == 284)
s.add(n[0] + n[4] + n[6] == 239)
s.add(n[41] + n[52] + n[11] == 315)
s.add(n[18] + n[42] + n[10] == 315)
s.add(n[3] + n[55] + n[34] == 333)
s.add(n[27] + n[45] + n[43] == 338)
s.add(n[25] + n[51] + n[39] == 321)
s.add(n[16] + n[35] + n[4] == 290)
s.add(n[4] + n[28] + n[59] == 306)
s.add(n[5] + n[44] + n[31] == 295)
s.add(n[6] + n[56] + n[58] == 276)
s.add(n[14] + n[22] + n[25] == 300)
s.add(n[51] + n[4] + n[36] == 284)
s.add(n[2] + n[38] + n[5] == 296)
s.add(n[11] + n[40] + n[49] == 336)
s.add(n[35] + n[38] + n[31] == 317)
s.add(n[23] + n[34] + n[5] == 295)
s.add(n[1] + n[5] + n[52] == 307)
s.add(n[46] + n[26] + n[33] == 298)
s.add(n[13] + n[1] + n[23] == 311)
s.add(n[49] + n[36] + n[50] == 313)
s.add(n[39] + n[25] + n[16] == 313)
s.add(n[58] + n[36] + n[18] == 322)
s.add(n[31] + n[7] + n[28] == 338)
s.add(n[21] + n[35] + n[45] == 333)
s.add(n[24] + n[46] + n[33] == 299)
s.add(n[29] + n[15] + n[0] == 292)
s.add(n[26] + n[5] + n[23] == 283)
s.add(n[10] + n[52] + n[39] == 319)
s.add(n[7] + n[12] + n[44] == 334)
s.add(n[50] + n[27] + n[29] == 301)
s.add(n[33] + n[22] + n[43] == 320)
s.add(n[45] + n[49] + n[10] == 338)
s.add(n[42] + n[58] + n[57] == 326)
s.add(n[59] + n[10] + n[12] == 331)
s.add(n[18] == 110)
r = s.check()
if r == sat:
m = s.model()
flag = ''
for i in range(60):
flag += chr(m[n[i]].as_long())
print flag
fwopCTF{quite_a_long_flag_for_reverse_eng_dont_you_think_so}
Reversing Python 8 (Reverse 500)
スクリプトでは、フラグの長さが27であるかをチェックし、ある法則でシャッフルしている。法則を整理するのが面倒なので、異なる文字27文字をシャッフルさせ、その結果から元に戻すようにする。
import string
enteredFlag = string.ascii_lowercase + '0'
coolarray = [[[], [], []], [[], [], []], [[], [], []]]
for i in range(3):
for j in range(3):
for k in range(3):
coolarray[i][j].append(enteredFlag[i*9 + j*3 + k])
newflag = ""
for i in [coolarray[2], coolarray[0], coolarray[1]]:
for j in i[::-1]:
for k in [j[1], j[2], j[0]]:
newflag = newflag + k
enc = "s}ginh_td{aFCTpwofolhs_yrar"
flag = ""
for i in range(len(enc)):
index = newflag.index(enteredFlag[i])
flag += enc[index]
print(flag)
fwopCTF{arrays_hold_things}
A street named what? (OSINT 100)
写真にあるAppleのロゴのところに記載されている場所の名前は「Apple Park Visitor Center」その前の通りの名前を答える。
fwopCTF{Pruneridge}
The Rock (OSINT 200)
"The Rock"の映画を調べると、アルカトラズ島を占拠したアメリカ海兵隊の英雄率いるテロリストと、制圧する特殊部隊との攻防を描いた作品とのこと。念のために、アルカトラズ島を調べると、以下の位置で写真と似たような景色が見えた。
https://www.google.co.jp/maps/@37.8256032,-122.422231,2a,75y,355.28h,95.7t,360r/data=!3m6!1e1!3m4!1sq2Sui4ey80V-GY6I_Gp6sg!2e0!7i13312!8i6656?hl=ja
fwopCTF{Alcatraz}
Location Location (OSINT 200)
問題には緯度、経度の計算結果らしきものがある。
>>> a = 10.9219612
>>> b = -19.712993
>>> x = (a + b) / 2
>>> y = (a - b) / 2
>>> x
-4.3955159
>>> y
15.317477100000001
xが緯度、yが経度として、調べる。
https://www.google.co.jp/maps/place/4%C2%B023'43.9%22S+15%C2%B019'02.9%22E/@-4.3955105,15.3152884,17z/data=!3m1!4b1!4m5!3m4!1s0x0:0x0!8m2!3d-4.3955159!4d15.3174771?hl=ja
Kinshasa
Kevin Gaming (OSINT 200)
このKevinさんが誰のことなのか、Twitterのツイートをヒントに探してみたが、わからない。適当にゲーム機の名前を入れたら、通った。
fwopCTF{PlayStation_2}
Kevin Took The Flag (OSINT 250)
Internet Archiveで見てみると、202/7/3に2回スナップショットが取られている。17:42:10のものを見てみると、フラグが書いてあった。
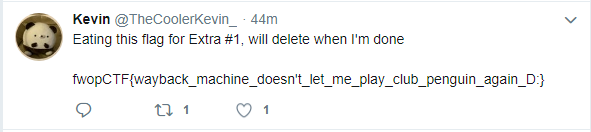
fwopCTF{wayback_machine_doesn't_let_me_play_club_penguin_again_D:}
Kevin's secret (OSINT 275)
$ git clone https://github.com/fweefwopkevin/country-flags
Cloning into 'country-flags'...
remote: Enumerating objects: 5368, done.
remote: Counting objects: 100% (753/753), done.
remote: Compressing objects: 100% (432/432), done.
remote: Total 5368 (delta 333), reused 663 (delta 321), pack-reused 4615
Receiving objects: 100% (5368/5368), 30.67 MiB | 8.04 MiB/s, done.
Resolving deltas: 100% (1295/1295), done.
Checking out files: 100% (1027/1027), done.
$ cd country-flags/.git
$ git log --all
commit 24b6c22afd7a18fe2a8343c8a94b364558946f1d (HEAD -> main, origin/main, origin/HEAD)
Author: fweefwopkevin <92276932+fweefwopkevin@users.noreply.github.com>
Date: Sat Oct 16 20:07:42 2021 -0700
Flag was redacted
commit 7c568d775c7363e9f86681452a5f85bcb4a12f10
Author: fweefwopkevin <92276932+fweefwopkevin@users.noreply.github.com>
Date: Sat Oct 16 20:06:41 2021 -0700
Create flag.txt
commit 6c887625a427c760099d993d56894be274d30b4f
Author: Wyatt O'Day <wyatt@wyday.com>
Date: Fri Sep 24 13:20:18 2021 -0400
Reduce flag of India size. Visually unchanged.
commit ec8815a9ead98e2f86cc871b8493b9c99f7e5c0c
Merge: 5746d5a 02289f2
Author: Wyatt OʼDay <wyatt@wyday.com>
Date: Fri Sep 24 11:56:08 2021 -0400
Merge pull request #123 from ronak69/main
Update Flag of India
$ ls -lR objects/
objects/:
合計 0
drwxrwxrwx 1 root root 0 10月 25 11:02 info
drwxrwxrwx 1 root root 0 10月 25 11:02 pack
objects/info:
合計 0
objects/pack:
合計 31556
-r-xr-xr-x 1 root root 151376 10月 25 11:02 pack-db658f291b3914a22a01f2ae1e4bee8b074d2e79.idx
-r-xr-xr-x 1 root root 32161291 10月 25 12:09 pack-db658f291b3914a22a01f2ae1e4bee8b074d2e79.pack
objectディレクトリにオブジェクト本体はなく、packがあるので、レポジトリを作ってそこで展開する。
$ cd ../..
$ git init newrepo
Initialized empty Git repository in /XXX/XXX/XXX/newrepo/.git/
$ cp -p ../country-flags/.git/objects/pack/pack-db658f291b3914a22a01f2ae1e4bee8b074d2e79.pack .
$ git unpack-objects < pack-db658f291b3914a22a01f2ae1e4bee8b074d2e79.pack
Unpacking objects: 100% (5368/5368), done.
$ cd newrepo/.git
オブジェクトを見ていく。
$ python -c 'import zlib; print zlib.decompress(open("objects/7c/568d775c7363e9f86681452a5f85bcb4a12f10").read())'
commit 726tree 395463cf3af3f316a11517c3ccf04096b33801ee
parent 6c887625a427c760099d993d56894be274d30b4f
author fweefwopkevin <92276932+fweefwopkevin@users.noreply.github.com> 1634440001 -0700
committer GitHub <noreply@github.com> 1634440001 -0700
gpgsig -----BEGIN PGP SIGNATURE-----
wsBcBAABCAAQBQJha5NBCRBK7hj4Ov3rIwAAOj8IADPlfgN5Z5NjiDR98WzLYY6t
N5FMXs8VmlixgGQM6zc2Cy2fYDk9AaSi5FjmrCKQf/whXa20uH+JeAPFJAUfy0BU
G9seDitWl+z7rkKRVFQ6Woo7g7/1yeJR6I+aakwUKztdghpK5SKPd6IijPoMssDl
IQUs1dpuOqReyjqcorfKv6ocWQZISnO9FQd7nO7byhe7hpVJprLgayi439A4Z6sd
/ig7eLrKb680YsggYpumntFeBR+JlJ/XH9kgr4KIZfQgzAUzIstzjZkX+gFJzz2k
e073qA/FESn1NulL7Tuwr8IvKJbLrCtVkuT1ibnhTsx/X7VUwYzvDJEo1HoD2Wc=
=Ev3Z
-----END PGP SIGNATURE-----
Create flag.txt
$ python -c 'import zlib; print zlib.decompress(open("objects/39/5463cf3af3f316a11517c3ccf04096b33801ee").read())' | xxd -g 1
00000000: 74 72 65 65 20 33 36 33 00 31 30 30 37 35 35 20 tree 363.100755
00000010: 2e 67 69 74 69 67 6e 6f 72 65 00 44 45 c2 3f 86 .gitignore.DE.?.
00000020: c9 62 9d a6 28 aa 92 d4 36 6b b5 08 75 48 5e 31 .b..(...6k..uH^1
00000030: 30 30 36 34 34 20 52 45 41 44 4d 45 2e 6d 64 00 00644 README.md.
00000040: 02 4c 62 ff ed 0d fb e8 6c 23 50 f3 f5 87 d0 31 .Lb.....l
00000050: 04 75 fe d8 31 30 30 36 34 34 20 63 6f 75 6e 74 .u..100644 count
00000060: 72 69 65 73 2e 6a 73 6f 6e 00 9b a3 84 44 74 ce ries.json....Dt.
00000070: 0f 6b 13 0b 65 6b 8f 5c 53 6d d6 85 0f 5b 31 30 .k..ek.\Sm...[10
00000080: 30 36 34 34 20 66 6c 61 67 2e 74 78 74 00 0a 87 0644 flag.txt...
00000090: cb 2a d2 13 5b 69 25 76 fa 54 52 22 2f e8 72 27 .*..[i%v.TR"/.r'
000000a0: d9 85 31 30 30 36 34 34 20 70 61 63 6b 61 67 65 ..100644 package
000000b0: 2e 6a 73 6f 6e 00 0f 37 50 99 49 52 ad 14 f8 a3 .json..7P.IR....
000000c0: 65 4d c8 c8 8e eb 95 bf ee a9 34 30 30 30 30 20 eM........40000
000000d0: 70 6e 67 31 30 30 30 70 78 00 c2 bd 5f 01 2c 64 png1000px..._.,d
000000e0: c1 f1 17 5d 12 47 27 f6 e9 a8 ab 4d bb 71 34 30 ...].G'....M.q40
000000f0: 30 30 30 20 70 6e 67 31 30 30 70 78 00 31 aa 4f 000 png100px.1.O
00000100: 9b 0e 05 5b 05 cb 36 3a d1 e3 0a dd 21 7f 75 bf ...[..6:....!.u.
00000110: 63 34 30 30 30 30 20 70 6e 67 32 35 30 70 78 00 c40000 png250px.
00000120: 87 2d 1e a5 37 7c 60 45 0d a8 65 1c 53 25 d4 74 .-..7|`E..e.S%.t
00000130: 45 d9 2b da 34 30 30 30 30 20 73 63 72 69 70 74 E.+.40000 script
00000140: 73 00 11 8c 23 ca 1b 02 33 c9 69 0a 76 16 84 47 s...
00000150: dc c3 a8 04 65 b4 34 30 30 30 30 20 73 76 67 00 ....e.40000 svg.
00000160: 94 9e 68 e7 8d 07 08 9b 6a 53 ad a0 94 2c 9f 88 ..h.....jS...,..
00000170: b8 ee 2b 9b 0a ..+..
$ python -c 'import zlib; print zlib.decompress(open("objects/0a/87cb2ad2135b692576fa5452222fe87227d985").read())'
blob 29620Lorem ipsum dolor sit amet, consectetur adipiscing elit. Integer consequat tellus ligula, vitae vulputate urna mattis nec. Donec sollicitudin nisl diam, sit amet auctor elit congue ac. Vestibulum finibus sit amet justo quis volutpat. Phasellus lacus purus, lobortis nec metus nec, fringilla condimentum sem. Maecenas a tincidunt justo. Nulla facilisi. Proin egestas bibendum ligula id ullamcorper. Vivamus vel sollicitudin tellus, et imperdiet magna. Fusce iaculis gravida lorem ultricies rhoncus. Nulla a nulla faucibus, consequat felis ut, efficitur purus.
Aliquam semper id dui ac elementum. Integer et leo arcu. Nunc interdum, turpis a eleifend fringilla, massa ligula iaculis erat, dictum hendrerit mi urna sed ipsum. Praesent fermentum enim vel ante ullamcorper porta. Aliquam convallis semper est nec vehicula. Sed in orci neque. Nullam nec sapien diam.
Vivamus hendrerit condimentum ligula, at dictum urna. Curabitur in gravida turpis, non mollis orci. Class aptent taciti sociosqu ad litora torquent per conubia nostra, per inceptos himenaeos. Integer condimentum egestas nisi, sed ornare arcu porttitor eu. Nam dignissim leo a efficitur blandit. Donec tincidunt dignissim risus in pulvinar. Nam nec blandit tortor. Aenean vulputate urna augue, ut venenatis odio pulvinar et. Mauris viverra pharetra ex eget luctus. In libero arcu, congue ac nulla id, vulputate efficitur ex. Pellentesque habitant morbi tristique senectus et netus et malesuada fames ac turpis egestas. Nunc porttitor neque luctus nunc consectetur malesuada. Fusce accumsan tortor et odio pulvinar tristique. Integer at auctor enim. Praesent et libero ac est luctus lacinia.
Vivamus ut leo eu ante feugiat tristique egestas quis tortor. Nullam semper nisi in sagittis tincidunt. Aenean efficitur, ligula condimentum tempus iaculis, turpis tellus varius velit, in tempor libero nisi eget nisi. Praesent placerat dolor id efficitur eleifend. Nunc convallis tempus urna sed rhoncus. Integer facilisis interdum enim, nec feugiat dolor sodales vitae. Vivamus cursus eget est at congue. Morbi maximus viverra nibh mattis dignissim. Curabitur purus odio, tincidunt at vestibulum id, bibendum vel mi. Nunc commodo, nunc in efficitur aliquet, orci elit ultrices dolor, rutrum rutrum enim quam non justo. Duis feugiat ligula nec ipsum feugiat vehicula. Nam consectetur tincidunt libero quis tristique. Quisque volutpat justo ac diam viverra sagittis.
Quisque a gravida lacus. Pellentesque habitant morbi tristique senectus et netus et malesuada fames ac turpis egestas. Suspendisse sit amet enim commodo, sollicitudin nisi gravida, malesuada arcu. Curabitur id tellus semper, consectetur nisi vel, maximus erat. Nulla maximus, ante ac auctor placerat, libero nisi accumsan lectus, nec luctus lacus lacus vitae magna. Morbi venenatis arcu non fringilla efficitur. Orci varius natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Fusce tristique neque ligula, sed posuere tellus rhoncus in. Lorem ipsum dolor sit amet, consectetur adipiscing elit. In feugiat augue orci, nec malesuada mi elementum fermentum. Etiam sed risus nec nulla iaculis bibendum. Interdum et malesuada fames ac ante ipsum primis in faucibus.
Nam et quam vel erat facilisis placerat sed et libero. Nulla at sem eget nisl consectetur posuere non vitae eros. Vestibulum eget justo luctus, rutrum mi vel, tristique elit. Donec tempor tellus massa, quis blandit lectus eleifend at. Donec faucibus condimentum odio, ut interdum nunc sollicitudin a. Nunc sit amet eros id velit auctor viverra. Curabitur ultricies commodo velit, ac placerat mi vehicula sit amet. Etiam est nibh, dignissim non lorem ut, luctus laoreet nulla. Interdum et malesuada fames ac ante ipsum primis in faucibus. Duis non diam nec purus auctor elementum. Pellentesque elit leo, tristique sed auctor sed, condimentum in est.
Aliquam consequat, metus a dapibus tincidunt, turpis eros tincidunt tortor, vitae accumsan tellus purus ultricies justo. Duis dui dui, aliquet ac placerat vitae, viverra nec quam. Ut lacinia ultricies eros, consectetur viverra justo pellentesque sollicitudin. Integer sed mauris enim. Etiam bibendum dui nec felis tempus, nec viverra purus malesuada. Etiam at consequat ex. Sed et facilisis orci, vel consequat urna. Mauris lorem libero, commodo non purus id, tempor tincidunt mi. Suspendisse diam orci, faucibus ut pretium sed, egestas vel odio. Quisque nec consequat orci, ac pellentesque dui. Integer rutrum suscipit tempus. Vivamus ac accumsan dolor. Duis eleifend metus vitae odio rhoncus commodo.
Integer tortor elit, convallis vitae fringilla placerat, interdum sed nibh. Ut consectetur nulla ut eros pellentesque, eu varius enim sollicitudin. Curabitur egestas metus in laoreet gravida. Donec pellentesque, erat vitae placerat posuere, felis justo dignissim eros, sed aliquet tellus mi id nisl. Sed tristique mauris eu nulla elementum, ac rhoncus purus lobortis. Vestibulum mattis dictum nulla, mollis bibendum mauris tristique vitae. Etiam vel bibendum nisi. Suspendisse potenti. Nunc et convallis massa.
Nulla facilisi. Mauris consequat urna eu libero feugiat, ut semper nulla consectetur. Proin accumsan finibus arcu, sed elementum eros varius sit amet. Suspendisse orci sem, hendrerit nec feugiat consequat, vehicula ultrices lacus. Aenean leo est, tempor at nunc eu, pretium consequat felis. Vestibulum neque ligula, malesuada ut nunc et, pretium convallis ligula. Nulla quis ultrices erat.
Morbi efficitur eros et laoreet accumsan. Suspendisse consequat, arcu vel venenatis tincidunt, nunc lacus dictum nunc, nec bibendum lacus nunc a turpis. Vivamus dictum suscipit feugiat. Mauris ornare turpis non nisi convallis condimentum. Fusce nec lectus bibendum, consequat urna eget, scelerisque lectus. In viverra neque sit amet lacus lobortis iaculis. Pellentesque egestas mi sit amet mi vehicula, at sodales nisi rhoncus. Duis congue arcu lacus, id tincidunt erat facilisis in.
Integer ornare leo in volutpat luctus. Sed vulputate lectus at augue varius, at eleifend odio imperdiet. Proin placerat lobortis odio quis dictum. Praesent elementum arcu ante, nec eleifend massa condimentum vitae. Phasellus elementum tortor in pretium pharetra. Phasellus auctor consectetur rutrum. Aenean laoreet enim mi, quis vestibulum nulla varius eget. In tristique augue et semper sollicitudin. Nullam a condimentum neque. Donec vulputate auctor aliquam. Ut nulla lorem, suscipit vel nisi sed, sodales dignissim augue. Sed sagittis rutrum nulla auctor faucibus. Mauris faucibus justo eget elit euismod, sit amet vulputate dui elementum. Morbi placerat sit amet tortor et accumsan.
Duis ac condimentum lectus, in euismod sapien. Curabitur tincidunt sem arcu, nec bibendum neque fringilla eget. Morbi ut porta justo. Suspendisse sollicitudin et eros id vehicula. Aliquam vitae ipsum ac quam suscipit pretium a mollis risus. Cras quis orci mattis, laoreet quam eu, maximus eros. Vestibulum interdum sapien semper mauris aliquet, elementum viverra mauris mollis. Nullam eget tellus non metus dictum faucibus. Praesent at urna a dolor aliquet finibus. Aenean pretium hendrerit nisl, in lacinia ex congue a. Sed ligula leo, ultrices a mattis eu, cursus quis sem. Integer lacinia nibh at risus lobortis, a dictum augue malesuada.
Cras varius suscipit neque non auctor. Donec pharetra elit non quam vestibulum, ut tempor sem euismod. Aenean tincidunt odio vel sodales ultrices. Aliquam blandit est at varius sollicitudin. Praesent quis turpis et eros consectetur fringilla sit amet non mauris. Mauris suscipit rhoncus risus, non semper lorem porttitor quis. Nam porttitor lectus non tortor bibendum dignissim. Quisque vitae nibh vel justo ullamcorper malesuada ut et mi.
Donec interdum convallis est sit amet faucibus. Duis laoreet mauris in mauris molestie, ut porta ante mollis. Sed in bibendum sapien, ac tempor turpis. Nullam finibus, purus a elementum consequat, risus tortor finibus lacus, id condimentum lectus libero quis justo. Sed hendrerit mi purus, ut ultricies eros bibendum convallis. In consequat purus ipsum, pulvinar vehicula odio consequat sed. Etiam convallis fringilla eros nec gravida.
Donec cursus diam et est suscipit, in mattis arcu rhoncus. Nam cursus leo vel lorem rutrum, eu efficitur magna tristique. Cras ut lobortis arcu. Vestibulum dignissim mi mauris, sed condimentum ipsum mollis eget. Aenean et purus rutrum, rutrum nisi sed, viverra mi. Cras nec sapien non turpis volutpat tincidunt in non ante. Praesent mattis elit id libero fringilla, sit amet dignissim turpis pretium. Fusce et nunc mi. Quisque pretium lobortis diam at consectetur. Morbi vel ultricies justo, vitae interdum nisl. Fusce congue massa quam, eu ullamcorper odio imperdiet ac. Integer sed massa sed justo eleifend volutpat non nec est. Cras lacinia vulputate maximus. Sed luctus pulvinar est ac volutpat. Pellentesque ut nibh sagittis lacus lacinia lobortis.
Donec egestas in nibh a dapibus. Donec lectus est, consequat et sem nec, egestas posuere metus. Vestibulum at neque placerat, hendrerit libero eu, mollis ipsum. Fusce pharetra ex mi, eget auctor felis cursus eu. Vestibulum ante ipsum primis in faucibus orci luctus et ultrices posuere cubilia curae; Aenean aliquet in est id interdum. Praesent laoreet ac arcu sed porta. Etiam ac feugiat arcu. Donec aliquam ex vel nisi tristique porta.
Nulla ut urna ante. Donec sed odio vitae sem euismod dignissim et consequat mauris. Curabitur volutpat ut velit sit amet imperdiet. Praesent pulvinar urna ut felis lobortis, ac dictum mauris varius. Aenean metus risus, placerat vel dui non, rutrum auctor purus. Nam nisl mauris, eleifend molestie accumsan vel, mattis ac lectus. Proin eleifend arcu ante, nec pretium libero volutpat non. Sed venenatis augue et felis sollicitudin, vel consequat nulla tincidunt. In vitae enim turpis. Aliquam condimentum, purus dapibus auctor cursus, sapien massa dignissim massa, et vulputate velit augue ut felis. Etiam eleifend ornare quam, sit amet laoreet lorem aliquam at. Vivamus leo magna, commodo sit amet orci eu, suscipit efficitur odio. Cras ac tristique urna.
Nullam eu lorem lobortis, ullamcorper ante vitae, tempus sapien. Fusce id placerat nisi, id auctor massa. Etiam id condimentum erat, ac vehicula enim. Nam placerat eu dolor ornare interdum. Mauris nec felis urna. Maecenas eget viverra libero. Nulla suscipit lorem eleifend diam commodo ultricies. Donec eu mollis erat.
Vestibulum lacinia ut nunc ut aliquet. Donec fermentum ultrices magna non pretium. Cras sit amet purus fringilla, dignissim lectus consequat, posuere quam. Vivamus a arcu elit. Sed ac elementum purus. Phasellus diam ipsum, feugiat in vulputate dictum, bibendum sit amet lacus. Sed sit amet rutrum nisi. Duis sit amet nisi lectus. Vestibulum quis egestas justo, laoreet accumsan tellus. Vestibulum erat eros, vulputate nec rutrum non, vestibulum at nunc. Mauris scelerisque vitae diam quis rutrum. Suspendisse venenatis metus facilisis ullamcorper efficitur. Suspendisse tincidunt enim mi, vel mattis ante hendrerit et. Nam scelerisque varius nunc, sit amet tincidunt leo. Praesent sed enim in felis ornare tincidunt posuere vitae ipsum. Donec scelerisque placerat metus.
In euismod, est ut aliquet auctor, nisl metus sollicitudin eros, ut gravida tellus nisi quis dolor. Phasellus non diam fermentum mauris maximus sodales. Vivamus eu venenatis augue, a tempor ante. Quisque orci est, aliquam vitae egestas id, gravida sed metus. Maecenas bibendum, nisi sed euismod porta, mauris dolor rhoncus sapien, sit amet luctus augue magna quis enim. Maecenas sagittis dictum tortor non sodales. Morbi diam lectus, mollis vitae justo vel, venenatis efficitur justo. Vestibulum efficitur eget velit in consectetur. Nunc ac interdum nisl, sit amet pharetra lectus. Aenean suscipit a ipsum eu varius. Praesent tortor urna, lacinia ac ultricies ut, lacinia sed metus. Nam malesuada odio sit amet sollicitudin sagittis. Nulla congue laoreet odio ac dignissim.
Cras lobortis nisl nibh, vitae aliquam eros volutpat in. Nam mattis ligula a ultrices commodo. Duis in diam in nulla tempor sollicitudin feugiat nec diam. Integer vitae blandit massa. Pellentesque tincidunt justo quis turpis ultricies, nec varius est imperdiet. Maecenas feugiat sapien a tellus semper, ut ornare tellus consectetur. Vestibulum pretium pulvinar erat, sed fringilla nisl maximus id. Mauris maximus risus est, sit amet tempus orci sodales ac. Vivamus non arcu et risus lacinia cursus. Etiam congue mi sed enim blandit cursus. Morbi libero ipsum, vestibulum aliquam arcu ac, porttitor molestie felis. Orci varius natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Sed dictum laoreet velit, eu ornare justo luctus sit amet. Nulla venenatis sapien eu sem venenatis, nec ultricies leo venenatis.
Flag: fwopCTF{h1dd3n_1n_7h3_h1570ry_28934}★
Mauris ut felis ac ipsum scelerisque sodales. Nullam nec varius est. Suspendisse mattis urna ut magna ullamcorper, id vestibulum tellus ultricies. Praesent nunc velit, congue in pretium in, auctor a dui. Nulla feugiat convallis orci rutrum dictum. Duis at placerat quam. Nunc porta arcu vel fermentum tempor. Morbi non sapien vitae purus rhoncus rhoncus. Suspendisse faucibus leo sed laoreet ultricies. Pellentesque a eleifend risus, vel blandit eros. Pellentesque habitant morbi tristique senectus et netus et malesuada fames ac turpis egestas. Pellentesque molestie urna et libero efficitur, eget ultrices eros fermentum. Orci varius natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus.
Pellentesque mollis, orci et imperdiet congue, magna tortor varius massa, ut faucibus augue elit id velit. Vestibulum suscipit in nunc sit amet pulvinar. Integer pretium, nulla non ornare scelerisque, nibh sapien aliquet nibh, eu posuere elit eros quis tortor. Nunc in fringilla tortor, a sollicitudin lorem. Phasellus et mi a ligula vehicula varius. Nullam vel condimentum dolor. Donec sollicitudin lacinia eros nec consectetur. Praesent vestibulum cursus facilisis. Vestibulum sagittis ac velit nec finibus. Suspendisse potenti. Pellentesque at tempus erat. Quisque a turpis a tellus vehicula ultrices quis ut dui. In molestie lobortis ipsum, eget posuere leo dictum nec.
Proin rhoncus urna massa, sit amet dictum purus tincidunt vitae. Aenean et ligula at risus euismod finibus. Sed dictum nec neque eu lobortis. Fusce tincidunt sodales metus, eu pharetra lorem fringilla consectetur. In tincidunt condimentum tincidunt. Aenean consequat est sit amet odio auctor imperdiet. Pellentesque et dolor ligula. Orci varius natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Aliquam sit amet feugiat dolor. Quisque congue condimentum eleifend. Morbi sed pellentesque nulla. Nullam interdum pellentesque lacinia. Curabitur eget mauris in tortor feugiat porttitor. Sed sit amet erat ac purus vehicula fringilla.
Morbi volutpat eget magna a finibus. Vestibulum eu odio sit amet lorem finibus vehicula. Aenean tempor mattis neque quis aliquet. Vestibulum egestas pulvinar tempus. Donec semper gravida augue a luctus. Suspendisse nec massa ultrices, laoreet odio vel, porta arcu. Aliquam ut nisi et leo maximus volutpat nec vitae turpis. Etiam accumsan sed eros gravida venenatis. In blandit metus eget malesuada lobortis. Nam porta, ligula quis blandit rhoncus, odio orci posuere ante, ut semper risus nulla eget massa. Suspendisse fermentum sit amet ligula nec dapibus. Donec vel volutpat orci, sit amet laoreet purus. Aliquam sagittis risus molestie pharetra pharetra. Nam id finibus lorem. Integer suscipit quis nunc a fringilla.
Sed eu purus aliquam, placerat erat sodales, malesuada turpis. Quisque placerat condimentum arcu vehicula eleifend. Nunc ac dignissim massa. Nam sed nisl nisl. Vestibulum purus nisi, lobortis et velit nec, bibendum interdum mi. Suspendisse vitae gravida lorem. In rutrum consectetur molestie. Donec mollis suscipit ultricies. Nullam in nunc efficitur, laoreet tellus a, dictum arcu. Ut dictum viverra enim, nec hendrerit sapien porttitor sit amet. Nulla dapibus aliquam tortor, vitae fermentum mauris eleifend vel. Vivamus dapibus feugiat augue. In lobortis id quam at bibendum.
Praesent purus eros, laoreet vitae tristique ac, fermentum a ante. Donec sit amet lacinia nisi. Vivamus sit amet sodales velit. Mauris eget sollicitudin risus. Nullam in sapien lacinia, tincidunt nunc quis, ornare lorem. Vestibulum maximus nisl in enim iaculis, at placerat nisl scelerisque. Quisque consectetur velit vitae lectus ornare fermentum. Integer justo augue, mattis vel venenatis luctus, ultrices a leo. Donec id tincidunt diam, vitae hendrerit sem.
Praesent vel ex purus. Nullam convallis augue et turpis tempor feugiat. Cras sed maximus turpis. Fusce tincidunt dapibus mattis. Proin vitae dolor tincidunt, scelerisque est ac, bibendum est. Praesent rhoncus, dui at congue tristique, libero leo semper diam, ut lobortis ipsum risus sed lorem. Vestibulum rhoncus velit purus, eget pretium velit varius nec. Fusce luctus dignissim purus, nec convallis velit porta et.
Morbi rutrum nisl vestibulum tincidunt mollis. Proin volutpat bibendum risus et luctus. Morbi faucibus justo elit, rhoncus ultrices enim egestas et. Proin varius sit amet dolor sit amet semper. Vestibulum in felis ut lectus iaculis ultrices. Morbi molestie vel velit at accumsan. Suspendisse eget felis sed lorem iaculis elementum. Nam et consectetur diam, sit amet blandit lorem.
Duis laoreet leo quis libero varius efficitur. Ut gravida orci non lectus posuere venenatis. Sed dapibus libero sit amet dui eleifend aliquam. Nunc tincidunt tortor eu tincidunt blandit. Nam non blandit dolor, eget suscipit nulla. Mauris gravida iaculis arcu, porta finibus est dictum quis. Sed condimentum scelerisque interdum. Curabitur sed dolor tristique, interdum augue sit amet, iaculis odio. Donec venenatis sodales arcu, at rhoncus sem rhoncus facilisis.
Nunc luctus ante dolor, id consequat erat pretium et. Cras ac orci volutpat, accumsan felis a, sollicitudin arcu. Integer vestibulum gravida orci, non convallis lectus gravida eget. Nulla vitae hendrerit metus. Suspendisse vehicula, ipsum eget finibus fermentum, nisl massa iaculis tellus, a malesuada leo nunc ac mi. Quisque sed libero et metus interdum porttitor. Aliquam elit nulla, rhoncus sit amet tortor eu, aliquet vehicula libero. Donec eu arcu mauris.
Aenean at purus eu purus molestie semper sagittis ut sapien. Donec pharetra ante non ornare vehicula. Vivamus a elit in odio ornare dictum. Pellentesque cursus, nibh vitae finibus mattis, odio justo lacinia eros, dignissim euismod justo ligula vitae neque. Suspendisse sollicitudin neque neque, et dictum velit pulvinar mattis. Suspendisse ornare sit amet orci quis dapibus. Vivamus ut ante ultricies, tincidunt metus ut, imperdiet sem. Suspendisse id justo ante. Nam sollicitudin, nibh et lobortis aliquam, odio est porta magna, hendrerit euismod massa metus ac sem. Etiam tristique turpis quis felis porttitor imperdiet. Nullam at vestibulum felis. Maecenas varius viverra ultricies. Aliquam sollicitudin nibh vel justo molestie, a pharetra magna iaculis. Sed non tincidunt sapien. Duis vel euismod libero.
Morbi nunc sem, placerat pellentesque tempor sed, vulputate et tellus. Duis eleifend et risus vel suscipit. Ut aliquet varius elementum. In et dolor vel quam commodo commodo non bibendum mauris. Cras volutpat mauris dui, vitae egestas massa scelerisque sed. Suspendisse sit amet turpis dignissim, blandit est et, congue nunc. Ut gravida tempor tempor. Cras convallis vulputate ante, a porta elit mollis ut. Nunc a lectus lectus. Aliquam ac viverra nisl. Duis a pellentesque est. Pellentesque tempor sodales gravida. Nam imperdiet mollis nibh, eu maximus libero. Vivamus vehicula egestas imperdiet. Mauris ullamcorper luctus tempor.
Nulla consectetur turpis eu posuere faucibus. Nunc nec ipsum massa. Nam ut iaculis dolor. Aliquam lectus tellus, consectetur varius dapibus ut, semper at augue. Vivamus nec magna nec enim consequat posuere nec sed ante. Cras posuere dignissim massa, nec viverra leo cursus ut. Pellentesque mattis rhoncus dignissim. Cras quis odio congue mauris consequat cursus. Pellentesque gravida elementum congue.
Nulla sollicitudin purus sed tincidunt tristique. Cras in vehicula nunc. Sed a malesuada massa, sed suscipit ipsum. Nulla dolor velit, porta ac leo id, porta pharetra neque. Donec porta orci nec ligula auctor sodales. Pellentesque habitant morbi tristique senectus et netus et malesuada fames ac turpis egestas. Nullam pretium gravida interdum. Proin quis nisl ut lacus dignissim sagittis. Aenean neque ante, blandit nec porttitor in, blandit ac odio. In commodo, dui nec efficitur gravida, nisi leo blandit dolor, ac volutpat elit justo in turpis. Suspendisse aliquet mauris id nibh dictum aliquam.
Curabitur ultrices magna nec ante finibus, vitae condimentum est tempor. Duis pulvinar pharetra felis, vel bibendum enim tincidunt eget. Mauris viverra, augue vel bibendum feugiat, purus libero placerat dolor, quis varius leo odio nec tellus. Etiam nisi sem, facilisis vitae lectus in, volutpat gravida dui. Suspendisse potenti. Aenean sit amet sagittis lacus. Sed ultricies faucibus interdum. Curabitur tortor quam, tristique a commodo id, aliquet sed mi. Mauris malesuada fringilla leo, ut viverra lacus. Mauris nec pharetra nisl. Quisque sit amet metus volutpat, porta lacus nec, posuere velit.
In malesuada hendrerit ligula, vitae consectetur arcu accumsan at. Nulla a bibendum justo. Duis eget suscipit nisl, sit amet varius nibh. Nunc fringilla, dui at dapibus vulputate, sem ante gravida risus, sit amet aliquet justo leo et erat. Ut gravida, arcu quis hendrerit eleifend, erat nisl fringilla ligula, at aliquet dolor enim non eros. Morbi congue, felis vitae vestibulum vehicula, felis odio tincidunt massa, quis lacinia risus mi in nibh. Vestibulum hendrerit imperdiet risus, vel scelerisque nisl elementum nec. Sed efficitur sem vitae consectetur convallis. Class aptent taciti sociosqu ad litora torquent per conubia nostra, per inceptos himenaeos. Nunc massa nibh, rutrum in sem sit amet, commodo pulvinar ipsum. Nulla pulvinar nibh lorem, nec posuere sapien cursus sed. Etiam rutrum lectus laoreet massa consequat aliquet. Phasellus vel luctus ante, et commodo massa. Nam egestas metus vel velit placerat, commodo eleifend mi mollis. Phasellus rhoncus dignissim diam. Quisque cursus ut ligula sollicitudin cursus.
Aliquam non diam ut nisi luctus suscipit vel sit amet est. Donec id pharetra odio. Curabitur tristique id ante suscipit luctus. Vivamus lobortis dictum ante, dignissim congue diam hendrerit at. Morbi aliquet est at mauris rutrum, varius vehicula urna rhoncus. Integer eu orci sapien. Phasellus sodales dignissim lectus sed varius. Sed varius consequat sapien, vel consectetur dui lobortis quis. Aliquam pharetra tortor id dictum molestie.
Fusce malesuada sagittis velit sed cursus. Donec porttitor lectus a mauris fermentum, vehicula interdum sapien faucibus. Proin sed ligula vel urna placerat vestibulum eget fermentum tellus. Aenean gravida nec quam ac blandit. Fusce dictum, libero id vulputate vestibulum, lectus diam iaculis lorem, et fermentum sem urna sit amet lacus. Praesent sed mi lacinia, laoreet erat sit amet, condimentum nunc. Vivamus feugiat diam tellus, sed mollis nisi vehicula nec. Etiam ultrices viverra tortor quis faucibus. Donec ornare ultrices tortor. Fusce tellus nulla, aliquet sit amet nisl ultricies, aliquet ultrices dolor. Donec nisi velit, facilisis id condimentum ac, aliquam in dolor. Quisque sagittis accumsan finibus.
Nunc nec dui non enim iaculis ornare. Quisque pharetra ipsum ut placerat suscipit. Etiam sapien velit, tempor ut risus a, placerat gravida augue. Nam auctor est quam, in aliquet arcu commodo ut. Duis viverra magna et lorem laoreet rhoncus. Phasellus eu aliquam orci. Cras non elementum velit. Vestibulum congue leo justo, eu varius purus semper convallis.
Pellentesque orci ante, venenatis et ipsum id, viverra bibendum tortor. Vestibulum sed libero at erat dignissim tincidunt tempor non metus. Morbi vel erat cursus, varius leo non, lacinia diam. Fusce sollicitudin urna at tortor rhoncus placerat. Aenean quis ante turpis. Sed quis semper eros. Nullam elementum euismod sem et tempor.
Nulla quis euismod tortor, a laoreet sem. Ut ornare non felis non sodales. Duis ipsum dolor, eleifend quis diam sit amet, ullamcorper dignissim orci. Nullam venenatis id leo quis rhoncus. Proin tincidunt mollis purus non dignissim. Duis sed nulla vitae dolor tempus tempus. Vestibulum justo purus, fermentum in nisi eget, placerat scelerisque tellus. Nam sagittis nisi non metus vestibulum, id feugiat ligula bibendum. Proin gravida quam ligula, sit amet semper mi vulputate sit amet. Praesent diam dolor, blandit at ornare congue, tempus nec neque.
Nulla suscipit nibh iaculis interdum dapibus. Cras non faucibus dolor, eget vehicula quam. Nullam in congue lectus, et ultricies nisl. Sed non dolor porttitor, imperdiet nulla at, auctor erat. Orci varius natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Fusce suscipit nisl ultricies, auctor odio eu, congue tortor. Pellentesque venenatis tortor id porta tempus. Duis lacinia nisl id diam tincidunt, nec iaculis lorem vestibulum. Cras maximus malesuada congue. Mauris at vulputate ipsum. Quisque ac elit semper, pellentesque nisi quis, vehicula mi.
Nam imperdiet urna nisl, sed dictum nunc pharetra vel. Nunc quis euismod ex. Phasellus at mauris scelerisque, vestibulum nisl quis, tincidunt eros. Cras ullamcorper, quam at porttitor consectetur, sapien nulla porttitor est, nec lacinia odio tellus rhoncus ante. Ut eu tortor ac sapien facilisis mattis. Maecenas tincidunt congue sapien. Morbi ultrices sem ligula. Donec eleifend velit diam, non condimentum lectus porta porta.
Mauris pulvinar sapien vitae lorem vehicula auctor. Nunc enim augue, placerat a magna vel, commodo laoreet tortor. Quisque blandit, tellus eu tincidunt accumsan, dolor orci sollicitudin libero, eu ullamcorper lectus felis tincidunt nisi. Nunc consectetur nulla vel enim pulvinar maximus. In ut semper arcu. Curabitur ex sem, feugiat a viverra sed, hendrerit sit amet risus. Integer tristique iaculis tellus, non porta nulla dictum et. In eget augue luctus, mollis ex quis, euismod augue. Nullam mi erat, mollis id porta sit amet, interdum vel odio. Vestibulum molestie, lacus in varius pretium, nisi turpis porttitor lorem, ac bibendum metus tellus in justo. Aenean diam felis, vehicula vel pharetra eu, ultricies in turpis.
Cras maximus dolor neque, id consectetur erat imperdiet lobortis. Etiam ultrices feugiat lorem in ultricies. Phasellus bibendum accumsan blandit. Morbi ac orci id magna ullamcorper eleifend interdum non est. Suspendisse interdum elit et luctus mattis. Aenean rutrum congue turpis eget hendrerit. Morbi finibus condimentum sagittis. Sed elit nunc, tempus euismod tempor et, fermentum sit amet libero. Fusce efficitur egestas massa vel dictum. In hac habitasse platea dictumst. Phasellus porta augue at orci aliquet pellentesque quis in neque.
Duis placerat lectus eget dignissim placerat. Class aptent taciti sociosqu ad litora torquent per conubia nostra, per inceptos himenaeos. Fusce arcu leo, gravida hendrerit felis id, lobortis venenatis neque. Morbi dui odio, bibendum eu elementum ut, aliquet at metus. Vestibulum tristique, mauris quis viverra egestas, nunc mi auctor eros, in auctor dui nisi id diam. Vestibulum eu ullamcorper urna. Ut mattis eu nisl eu tristique. Etiam id sollicitudin dolor. Interdum et malesuada fames ac ante ipsum primis in faucibus. Quisque eu dignissim nibh. Nulla gravida ultricies neque efficitur consectetur. Donec vel sem dictum, condimentum metus et, ultrices dui. Sed aliquet ligula eu sem congue iaculis. Sed iaculis dolor ac mauris fermentum auctor. Morbi orci massa, finibus nec eros volutpat, blandit aliquet sapien. Donec scelerisque dui sit amet ipsum sollicitudin aliquet.
Suspendisse hendrerit purus sed libero posuere interdum. Aliquam tempor velit dolor, eget porttitor diam luctus eu. Duis sagittis sapien eu neque vulputate iaculis. Nullam nec fringilla turpis. Suspendisse purus mi, euismod non lacus eget, placerat ultrices ex. Curabitur mauris sapien, tincidunt sit amet dapibus vitae, mattis eget lacus. Morbi imperdiet ipsum elit, vitae placerat enim ullamcorper at. Sed condimentum lobortis ligula non tincidunt. Nullam semper arcu arcu, et rhoncus massa suscipit quis. Aenean nec tempus dolor. Maecenas quis purus quis turpis auctor scelerisque eu vitae purus. Etiam dapibus mauris vel ante sollicitudin imperdiet. Praesent a fringilla nisl, vitae bibendum enim.
Aliquam condimentum lacus convallis est auctor finibus. Aliquam et est ut lectus pulvinar cursus at sed nunc. Cras iaculis ultrices orci, et fringilla massa porttitor sed. Mauris id maximus dui, sit amet finibus tellus. Phasellus at interdum metus. Integer in sem magna. Aenean euismod dictum felis ut ultricies. Nunc dictum mi eu ullamcorper ultrices. Integer iaculis nulla venenatis ante aliquet dignissim. Donec a nulla faucibus, placerat odio tincidunt, imperdiet diam. Cras posuere at metus ac viverra.
Proin scelerisque scelerisque elementum. Praesent ut facilisis arcu. Proin congue, erat ut finibus commodo, justo dui luctus ante, eu dignissim metus ligula vitae tortor. Nulla facilisi. Donec vitae mi ligula. Ut dignissim rhoncus dictum. Praesent ornare, lacus a euismod lobortis, arcu tortor mattis diam, sed ullamcorper magna elit non orci. In sagittis massa tellus, varius interdum magna semper nec.
文中にフラグがあった。
fwopCTF{h1dd3n_1n_7h3_h1570ry_28934}